UHelp-Support Ticketing System
App Settings
- General Settings
- Ticket Settings
- SEO Setup
- Google Analytics
- Custom JS & CSS
- Captcha Settings
- Social Logins
- Email Settings
- External Chat
- Security Settings
- IP List
- Bot Response Setting
- Twilio Setting
- Payment Gateways
- AI Setup
- SSO Setup
1. General Settings
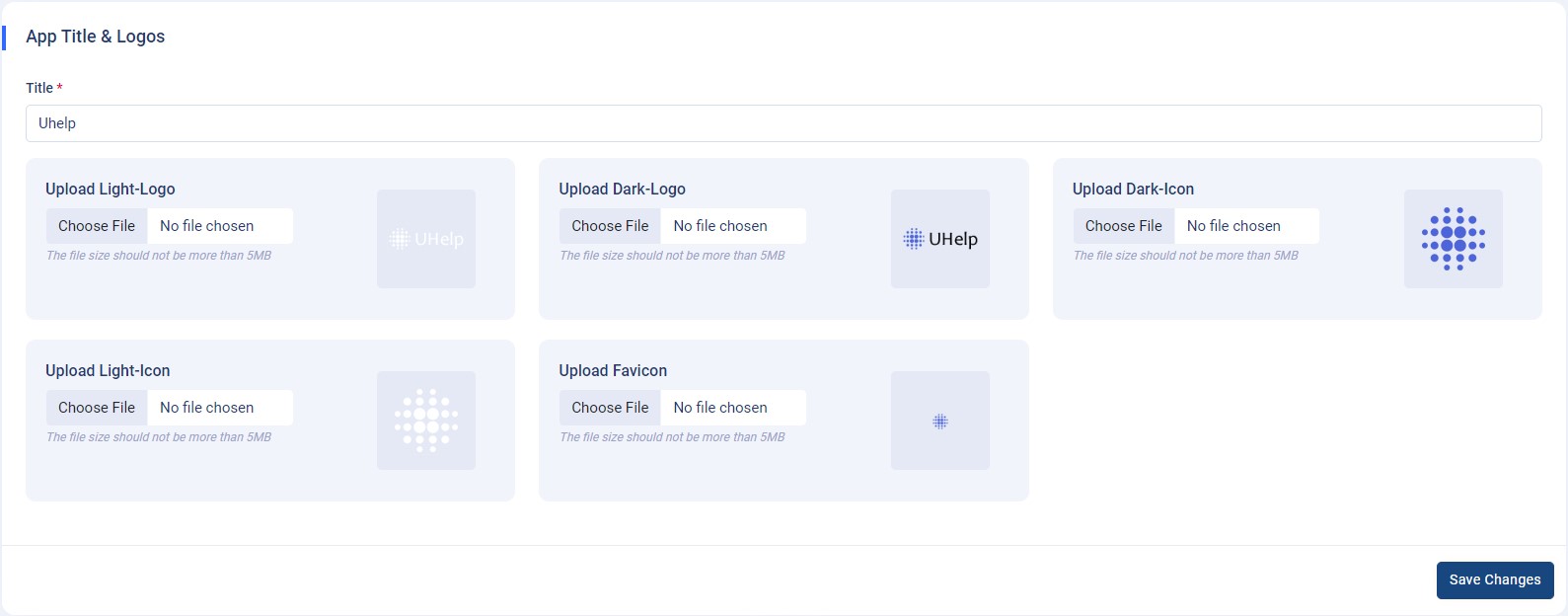
How to Setup “App Title and Logos”?
- Title : It’s the main title for the application. You can set the application's main title here by filling in the below input field with the "Title" name.
- Upload Light-Logo : You can upload your own brand "light logo" for the application to reflect this light logo in the dark theme.
- Upload Dark-Logo : You can upload your own brand "dark logo" for the application to reflect this dark logo in the light theme.
- Upload Dark-Icon : You can upload your own brand "dark icon" for the application to reflect this dark icon in the light theme.
- Upload Light-Icon : You can upload your own brand "light icon" for the application to reflect this light icon in the dark theme.
- Upload Favicon : You can upload your own brand "Favicon" for the application to reflect this Favicon the application.
Note : Please click on the “Save Changes” button
after uploading the title, logos, icons, and favicon.
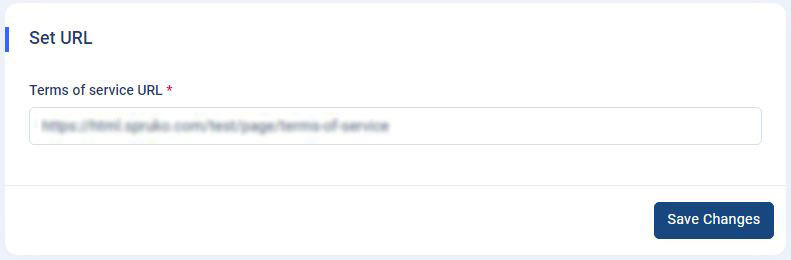
How to set URL for "Terms of Service" ?
-
Set URL : Go to the
Admin panel->App Settings->General Settings. There you will find a section called "Set URL" with an input field of "Terms of Service". - Terms of Service : Now type the "Terms of Service" url in the input field and click on the "Save Changes" button to reflect that url on the customer registration form and the customer "Delete Account".
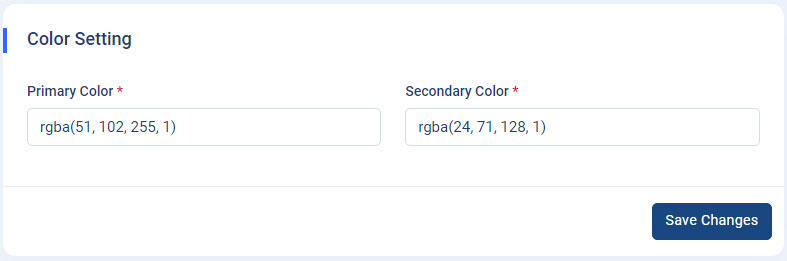
How to change the primary and secondary colors of the application globally?
-
Color Setting : Navigate to
Admin panel->App Setting->General Settings. You can update the "Primary and Secondary" colors of the application according to your choices with this setting. - Primary Color : To change the primary colour of your application, please click on the (RGBA) "Primary color" input field and set the color of your choice, then click on the "Save Changes" button to see the change on the application globally.
- Secondary Color : To change the secondary colour of your application, please click on the (RGBA) "Secondary color" input field and set the color of your choice, then click on the "Save Changes" button to see the change on the application globally.
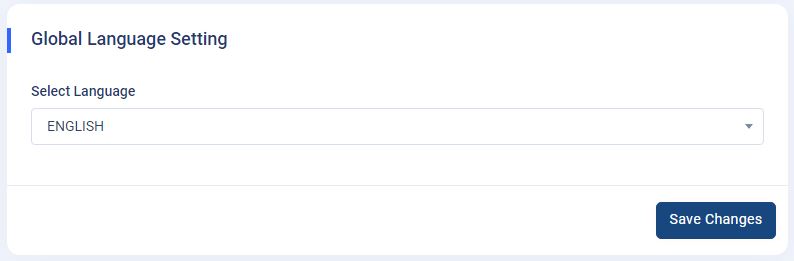
How to change the language and version (LTR to RTL) of the application globally?
-
Global Language Setting :
Navigate to
Admin panel->App Setting->General Settings. With this feature, you can change the application's "Language and Version" (LTR to RTL) according to your choices. - Language & Version : Here, by default, we provided a total of fifteen languages. For example, if you select the Arabic (AR) language from the language dropdown, then the whole application will convert into the Arabic language as well as change the version from LRT to RTL.
Note : Please click on the “Save Changes” button
after selecting the language.
How to change the Date and Time Formats of the application globally?
-
Global Date & Time Format:
Navigate to the
Admin panel->App Setting->General Settings. You can update the "Date and Time" formats of the application according to your choices with this setting. - Select Date Format : To change the date format of your application, please click on the "Select Date Format" dropdown and set the "Date Format" according to your choice, then click on the "Save Changes" button to see the change on the application globally.
- Select Time Format : To change the time format of your application, please click on the "Select Time Format" dropdown and set the "Time Format" according to your choice, then click on the "Save Changes" button to see the change on the application globally.

How to delete inactive customers and guests? and contact us settings
-
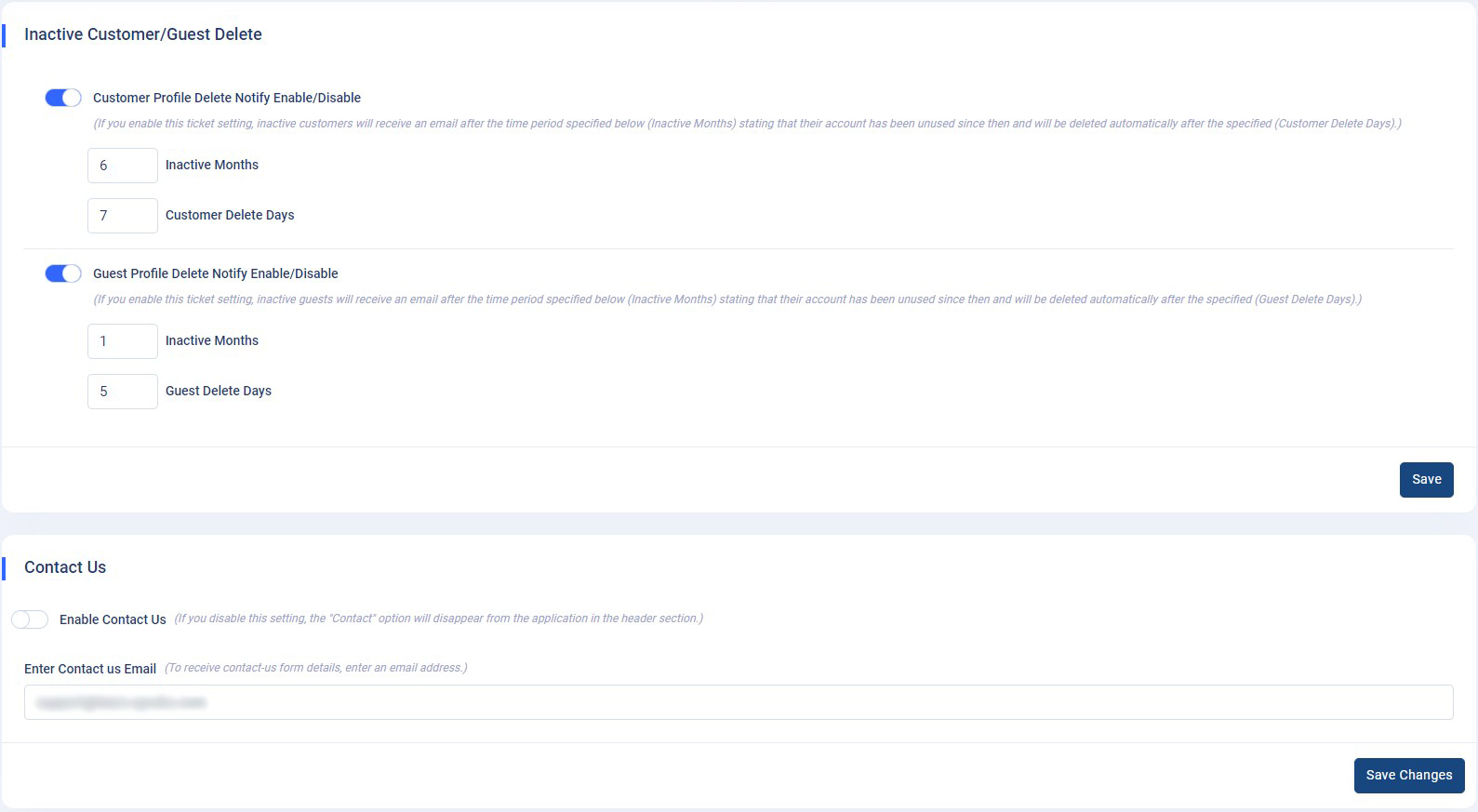
Inactive Customer/Guest Delete:
Navigate to the
Admin panel->App Setting->General Settings. Inactive customers/guests will receive an email after the time period specified (Inactive Months) stating that their account has been unused since then and will be deleted automatically after the specified (Customer/guest Delete Days). -
Contact Us : You will find a
switch to enable contact us on the main site. If the switch is
enabled, you will find contact us button on the landing page
There you will find an input field for the email to which you can get contact form details.
How to use Two Factor Authentication Settings?
-
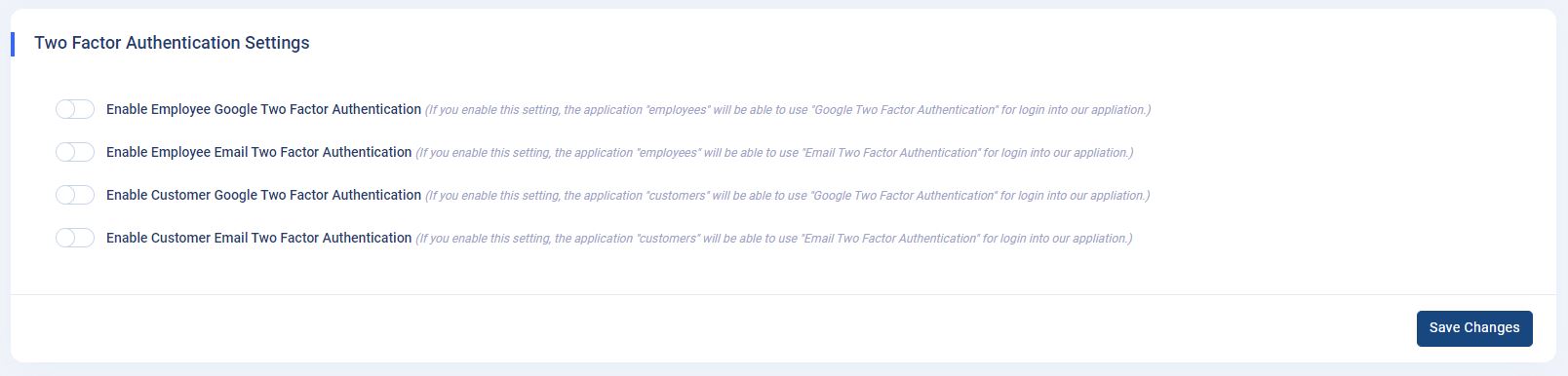
Two Factor Authentication
Settings: Within the
Admin Panel -> App Settings -> General Settingspage, the "Two Factor Authentication Settings" section allows administrators to configure authentication options for employees and customers. - Configuration Options:
- Four toggle switches are available:
- "Enable Employee Google Two Factor Authentication": Enables Google Two Factor Authentication for employee logins.
- "Enable Employee Email Two Factor Authentication": Enables Email Two Factor Authentication for employee logins.
- "Enable Customer Google Two Factor Authentication": Enables Google Two Factor Authentication for customer logins.
- "Enable Customer Email Two Factor Authentication": Enables Email Two Factor Authentication for customer logins.
-
Overview:
- "With these settings, administrators can enhance security by enabling Two Factor Authentication (2FA) methods for both employees and customers.
- "Google Two Factor Authentication utilizes Google Authenticator or similar apps to generate authentication codes.
- "Email Two Factor Authentication sends a verification code to the user's email address for login confirmation.
- "Administrators can tailor authentication settings based on the security requirements and preferences of their organization and users.
How to use Security Settings?
-
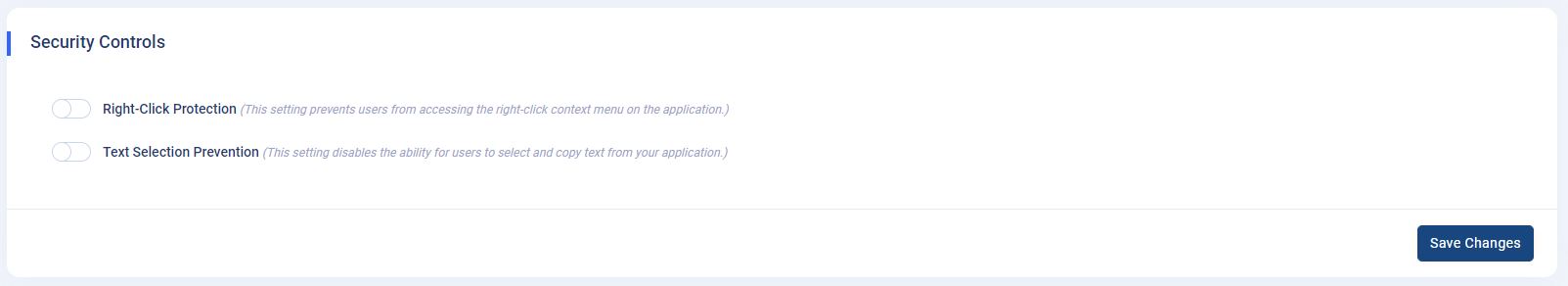
Security Settings: Located within
the
Admin Panel -> App Settings -> General Settingspage, the "Security Settings" section offers administrators control over specific security measures to safeguard the application. - Configuration Options:
- This section features two toggle switches:
- "Right-Click Protection": When enabled, users are prevented from accessing the right-click context menu within the application, enhancing protection against unauthorized actions.
- "Text Selection Prevention": Enabling this setting disables users' ability to select and copy text from the application, thereby safeguarding sensitive content.
-
Overview:
- These security settings provide administrators with tools to mitigate risks and protect sensitive information within the application environment.
- "Right-Click Protection" helps prevent unauthorized actions or data extraction by limiting users' access to context menu functionalities.
- "Text Selection Prevention" enhances data security by restricting users' ability to copy and extract text, minimizing the risk of unauthorized data replication or misuse.
How to use Session Timeout Settings?
-
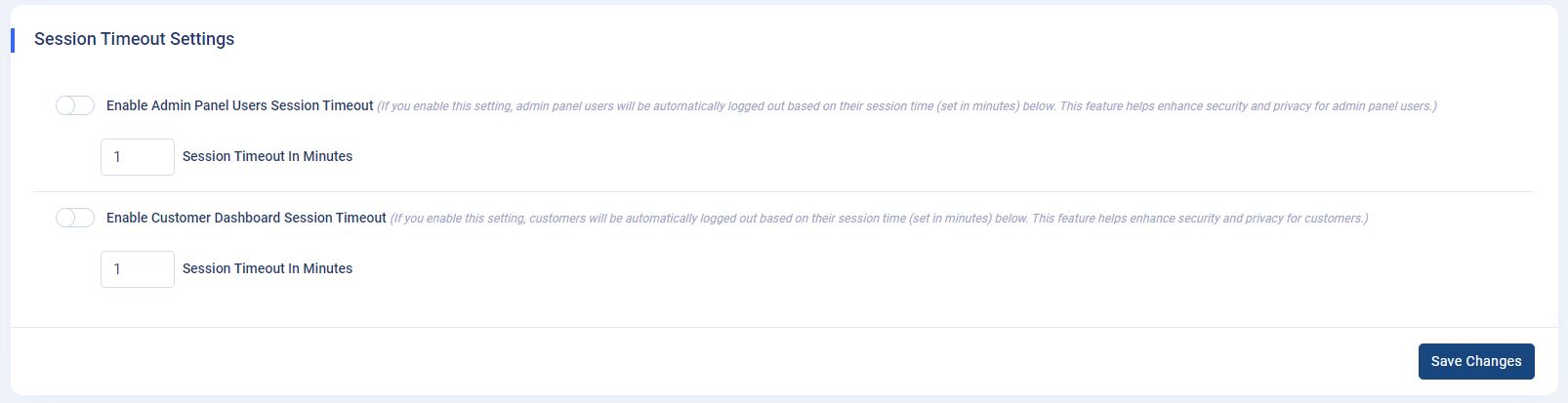
Session Timeout Settings: Found
within the
Admin Panel -> App Settings -> General Settingspage, the "Session Timeout Settings" section empowers administrators to manage session durations for both admin panel users and customers, enhancing security and privacy. - Configuration Options:
- This section comprises two toggle switches and corresponding input fields:
- "Enable Admin Panel Users Session Timeout": When activated, admin panel users will be automatically logged out after the specified session time, as set in the "Session Timeout In Minutes" input field. This feature enhances security by mitigating the risk of unauthorized access.
- "Enable Customer Dashboard Session Timeout": Activating this setting logs customers out after the designated session time, configured in the "Session Timeout In Minutes" input field. It bolsters privacy and security by ensuring inactive sessions are terminated promptly.
-
Overview:
- The "Session Timeout Settings" provide administrators with granular control over session durations, aligning with security best practices.
- Admin panel users and customers benefit from enhanced security and privacy, as sessions automatically expire after the specified timeout period, reducing the risk of unauthorized access to sensitive data.
- Configurable session timeout settings allow organizations to tailor security measures to their specific needs, promoting a secure and user-friendly experience for all users.
How to setup application global settings?
- App Global Settings : A clear explanation is given for each and every concept in this setting as shown in the below image.
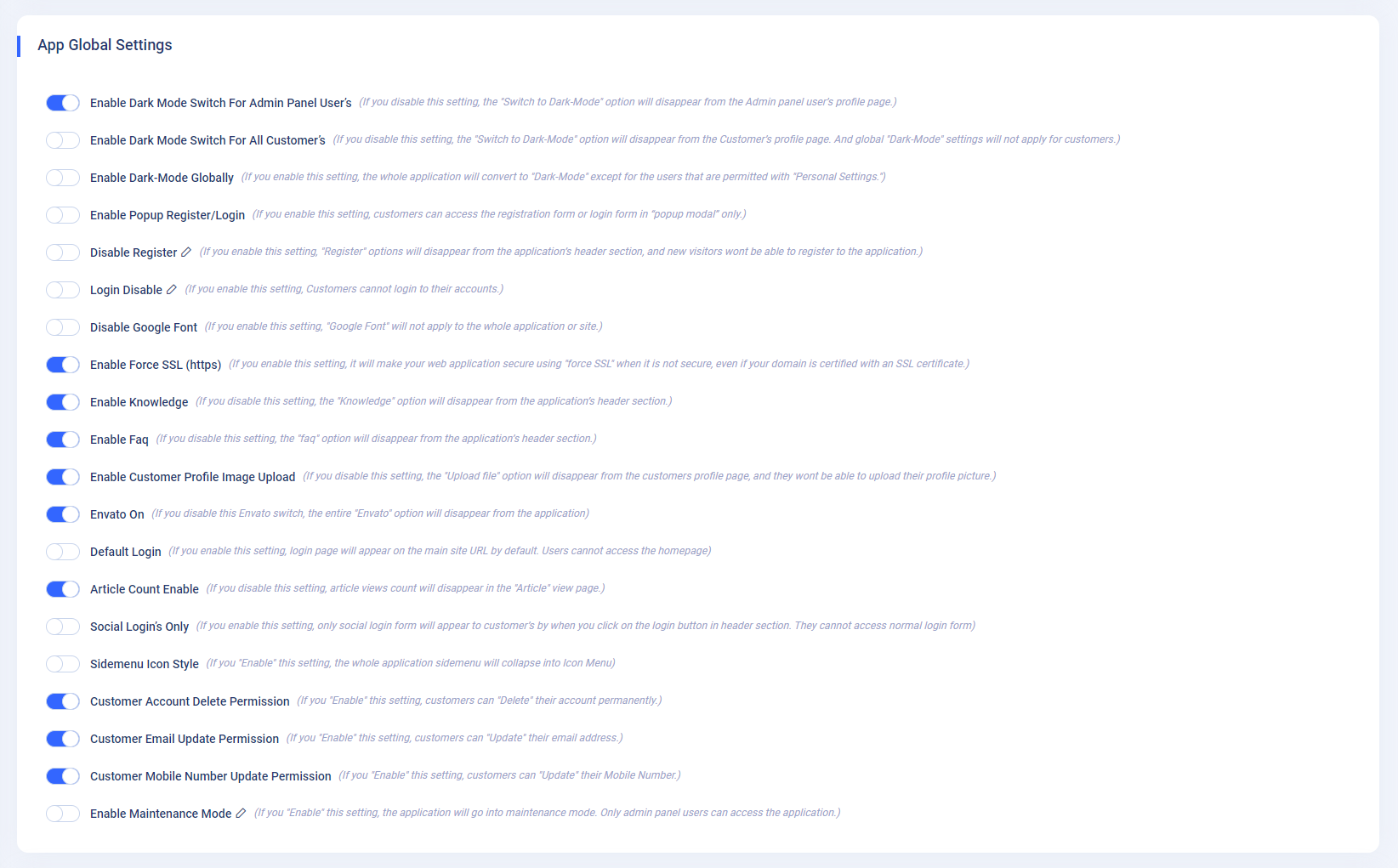
How to setup Two Factor Authentication?
- Two-Factor-Authentication A clear explanation is given for each and every concept in this setting as shown in the below image.
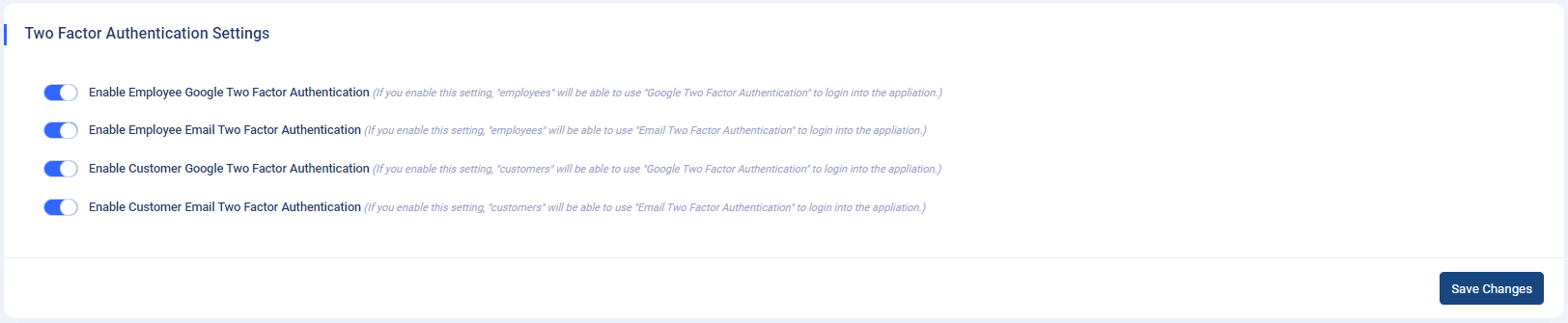
How to change footer text?
-
Footer Copyright Text : Navigate
to
Admin panel->App Setting->General Settings. Using the summer note editor, you can change the applications' footer text. As shown in the below image, - If you don’t want to display any content in the footer section, please leave it empty.
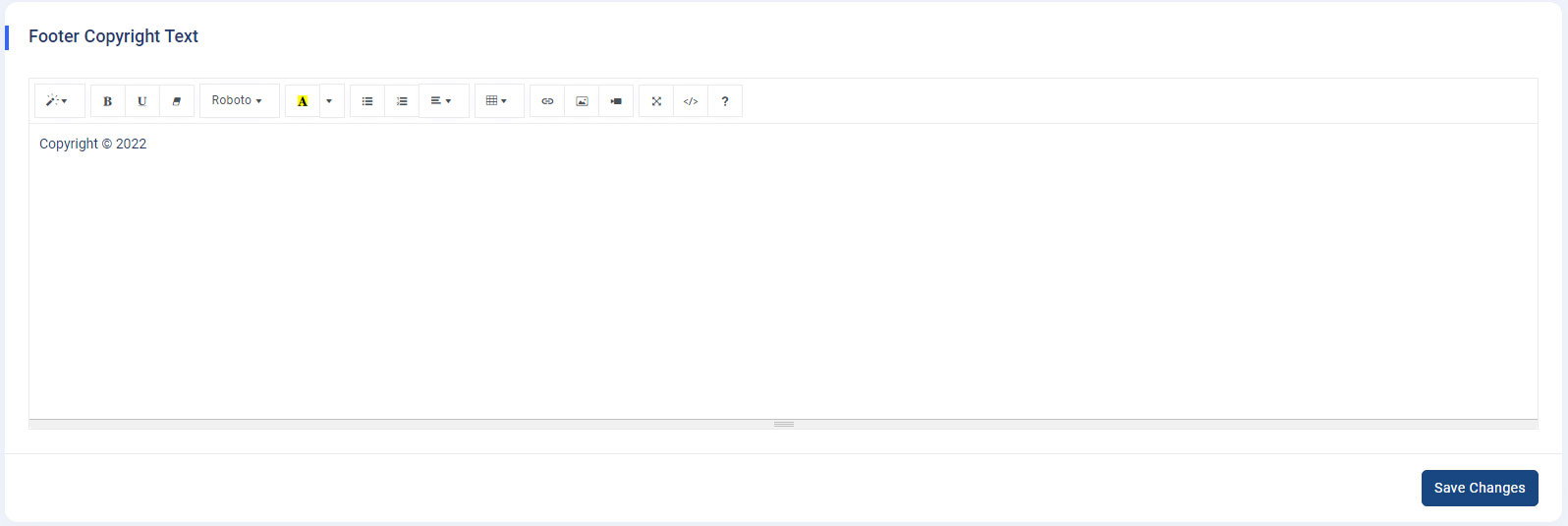
Note : Please click on the “Save Changes” button
after customizing the footer text in the summer note.
2. Ticket Settings
How to setup ticket settings?
-
Ticket Settings : Navigate to
Admin panel->App Setting->Ticket Settings. Please select options to control the ticket settings. Or else, you can also refer to the particular "Ticket Settings" page to get an overview of the ticket settings, example as shown in the below image.
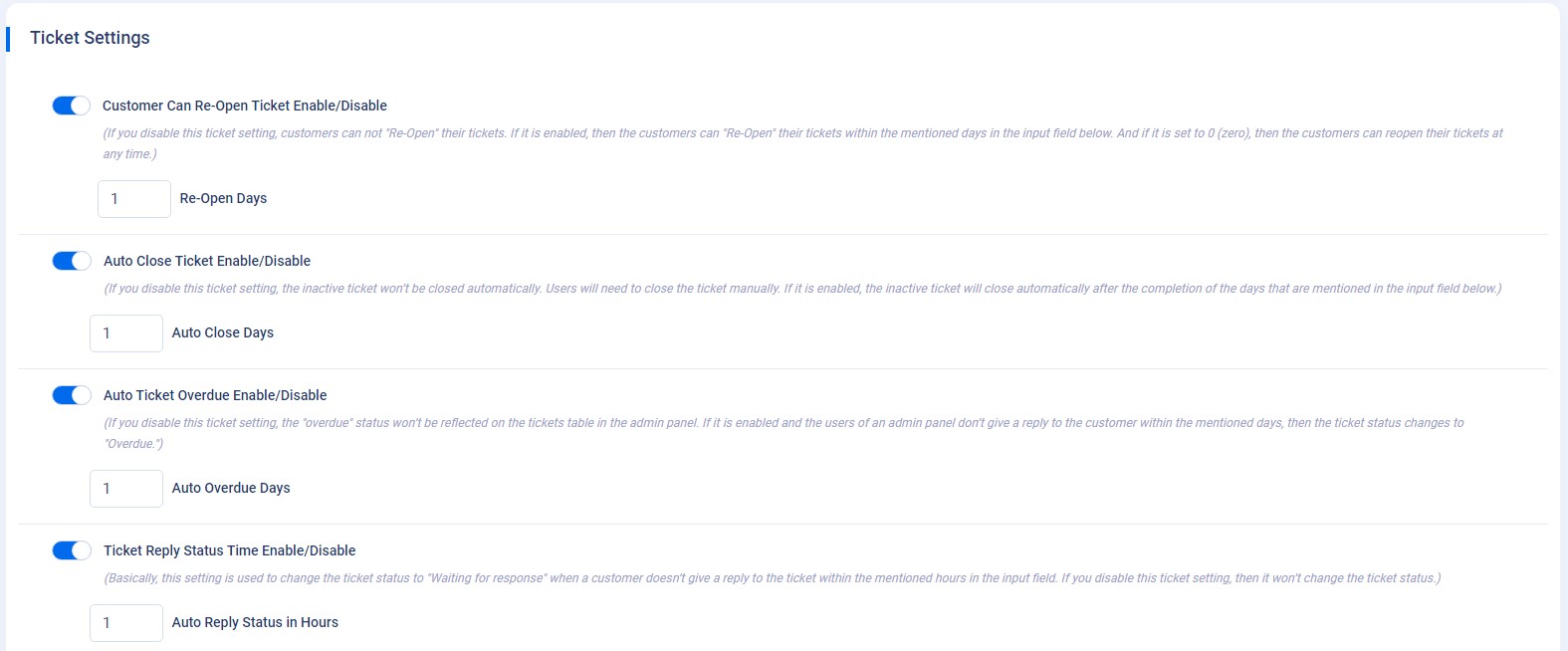
How to setup file settings?
-
File settings : Navigate to
Admin panel->App Setting->Ticket Settings. The "superadmin" or any other “employee” who has permission to access the admin panel can control the file size and file type that will be uploaded to the tickets or articles by users.Here, the superadmin or permitted employee can set the maximum files to be uploaded by users for tickets or articles. For example, if the "Max File Upload" option is set to 2 in the input fields by the admin, then the users can only upload a maximum of 2 images or files.
Here, the superadmin or permitted employee can set the maximum file size to be uploaded by users for tickets or articles. For example, if the file is set to 3MB by the admin, then the users can only upload images or files up to 3MB.
Here, the superadmin or permitted employee can set the file types to be uploaded by users for tickets or articles. For example, if the file type is set as .jpg or.png by the superadmin, then the users can only upload those types of images or files.
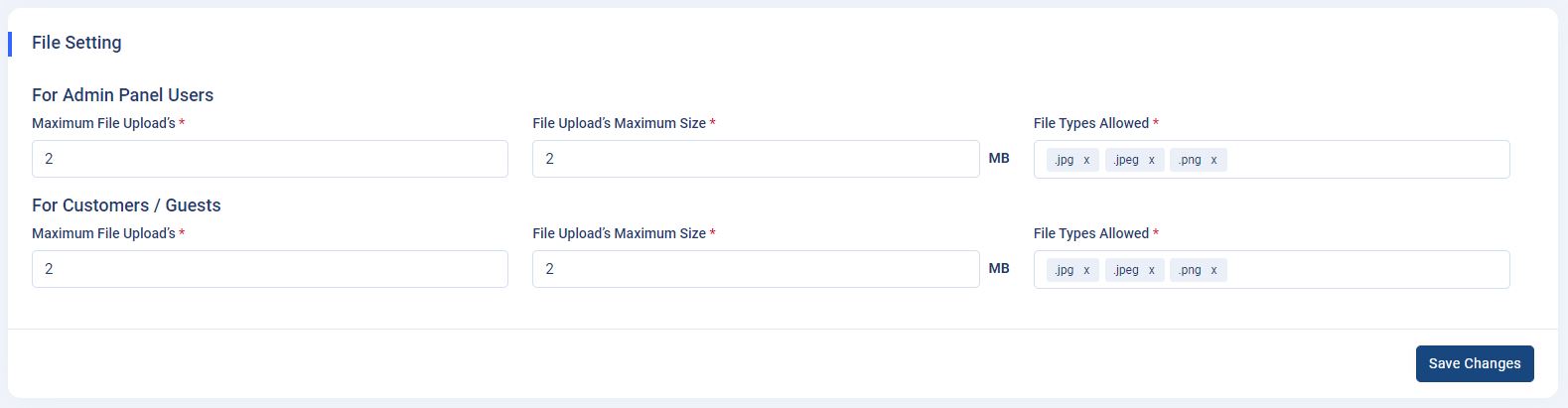
Note : Please click on the “Save Changes” button
after setting up your file settings.
3. SEO Setup
How to setup SEO setting?
-
SEO Settings : This web
application also provides you with SEO (search engine
optimization) settings. To setup SEO, navigate to
Admin Panel->App Setting->SEO. This SEO setup comes with three input fields. 1. The author, 2. The description, and 3. The keywords. Fill out those three input fields so that you can increase the traffic for the application.
4. Google Analytics
How to track the application’s activity using Google Analytics?
-
Google Analytics : Basically,
"Google Analytics" is used to track and monitor the
application’s activities and the flow of traffic. To use the
"Google Analytics" setting in the application, go to
Admin Panel->App Setting->Google Analytics. Now click on the toggle switch button of "Enable Google Analytics" to enable and type the "Tracking ID" in the input field and click on the "Save Changes" button to apply the changes.
5.Custom JS & CSS
-
Custom CSS and JavaScript : This
feature is used to customize the "CSS and JS." To use this
feature, navigate to
Admin Panel->App Setting->Custom CSS and JavaScriptand follow the below given instructions. - Custom CSS : Now you can customize your application styles by using custom CSS. And please do not use any tags, ex: , while writing CSS code.
- Custom JS : Now you can customize your application JavaScript by using custom JS. And please do not use any tags, ex: , while writing JS code.
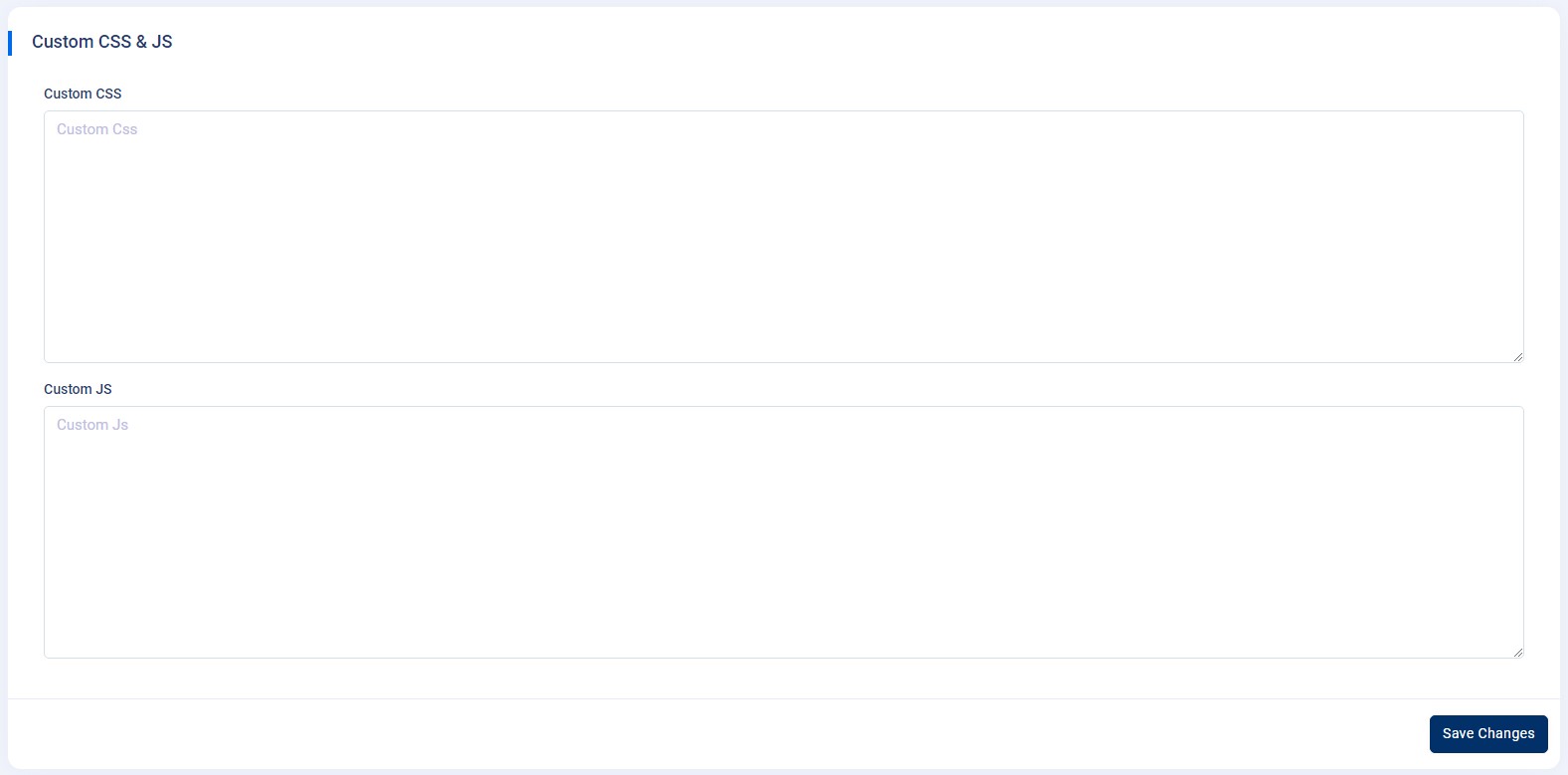
Note : Please click on the “Save Changes” button after
setting up your custom CSS and JS. .
6. Captcha Settings
How to setup Captcha setting?
-
Captcha Settings : This setting
protects against any system-generated attacks like DoS attacks.
To use this setting in the application, go to
Admin Panel->App Setting->Captcha Settingpage. - Captcha Disable : Both manual and Google reCaptcha settings are deactivated or disabled by default in the application. Two captchas cannot be used at the same time.
- Manual Captcha Enable : To enable "Manual captcha" in your application, simply click on the switch button. However, if you use manual captcha, the other one, "Google reCaptcha," will be automatically disabled.
-
Google Captcha Enable : If you
want to use "Google reCaptcha," you must first configure Google
reCaptcha's settings and get the "Site Key" and "Secret Key."
Please visit the official site to create those two keys: https://www.google.com/recaptcha/admin/create
and follow the instructions as given.
Assuming that you have generated a "Site Key" and a "Secret Key". Now copy those two keys and paste them in the input field of "Google Re-Captcha Setting" and click on the "Save Changes" button. To use Google reCaptcha in the application, please enable the “Google Captcha Enable” toggle switch button from the above section.Note: Please use only "reCAPTCHA v2" to generate "Site Key" and "Secret Key". -
Captcha Setting in Forms : You
must enable the switch of the forms as shown in the below image
if you wish to use one of the above two, "Manual Captcha" or
"Google reCaptcha" in them.
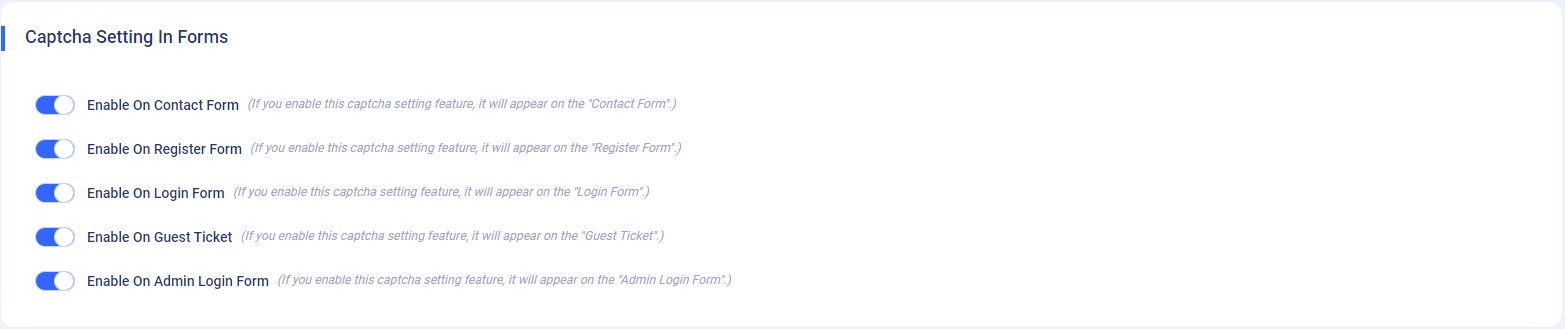
For example, if you want to use manual captcha in the above-mentioned forms, you must first activate the "Manual Captcha Enable" switch button from the above section, then enable the switch button of the forms where you want to use manual captcha.
7. Social Logins
-
Social Logins : This feature
gives "customers" an easy way to login to use the application.
To use this feature in the application, navigate to the
Admin Panel->App Setting->Social Loginspage and follow the below process. -
Social Login : By default, the
application comes with four (3) different types of social
logins: Envato, Google, and Microsoft logins. Using those social
login credentials, customers or users can easily login to the
application.
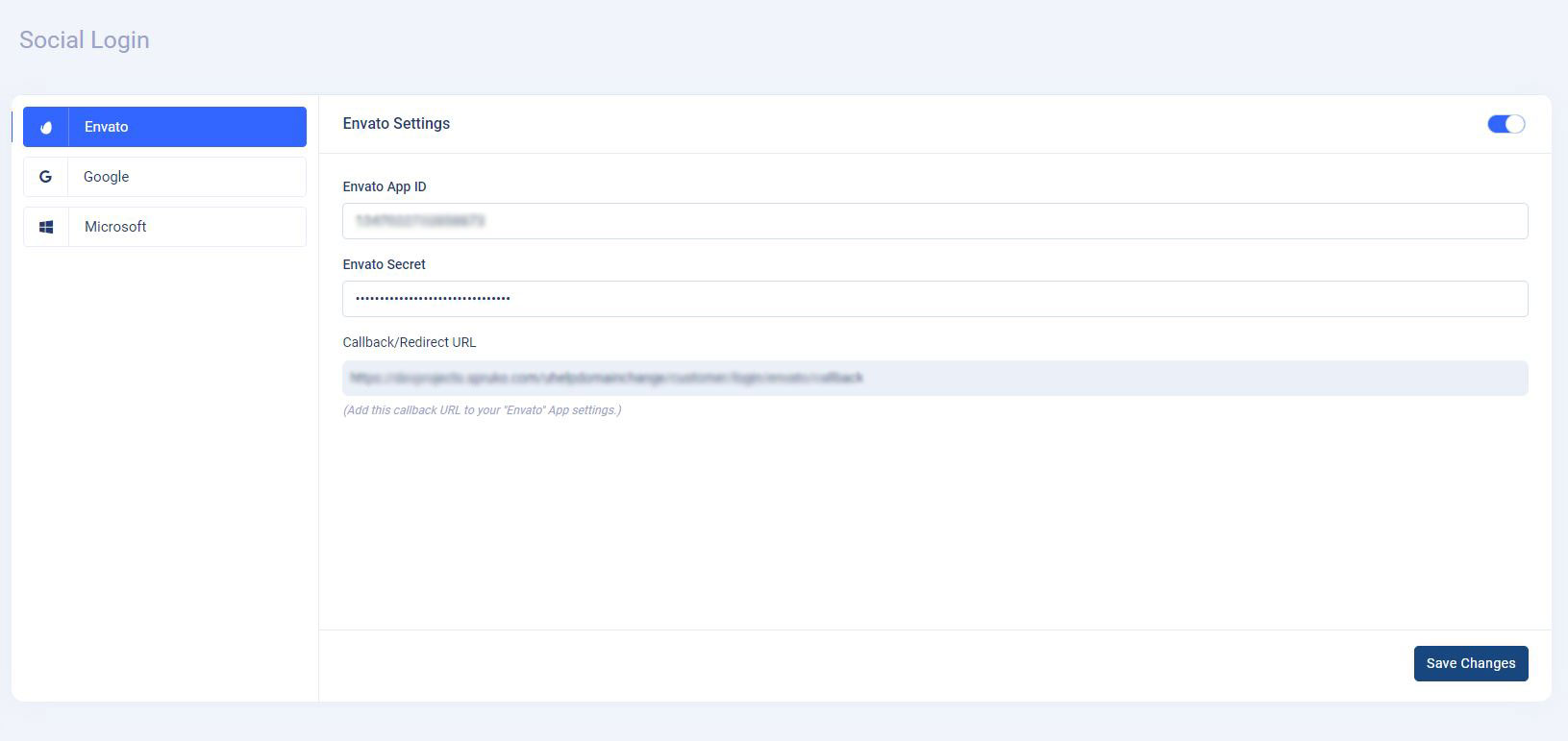
To use the above-mentioned social logins, for example, in my case, I chose the "Google" social login. Now go to the Google developer site and then you will need to configure and generate the "Client Id" and "Secret Id" for Google social login. Then, to show the Google social login on the application's login page, enter those two IDs into the input fields of the Google social login you generated, enable the switch, and click the "Save Changes" button.
8. Email Setting
-
Email Setting : This settings
page serves the purpose of facilitating the sending and
receiving of emails within the application, encompassing
SMTP/Send Mail and IMAP configurations. To set
up these parameters, kindly go to the
Admin Panel->App Setting->Email Setting, and finally access the Email Settings page. Follow the outlined process to configure the settings accordingly.
-
Send Test Mail : The application
offers a valuable feature called "Send Test Mail" that allows
you to preview how your emails will appear in your customers'
inboxes. To utilize this option, start by completing the
necessary details in the "SMTP/Send Mail" section provided
below. Once you've filled out the required information, you can
easily use the "Send Test Mail" option to assess the email's
presentation.
Now please enter a valid email address in the input filed and click the "Send" button to test the "Send Test Mail" option.
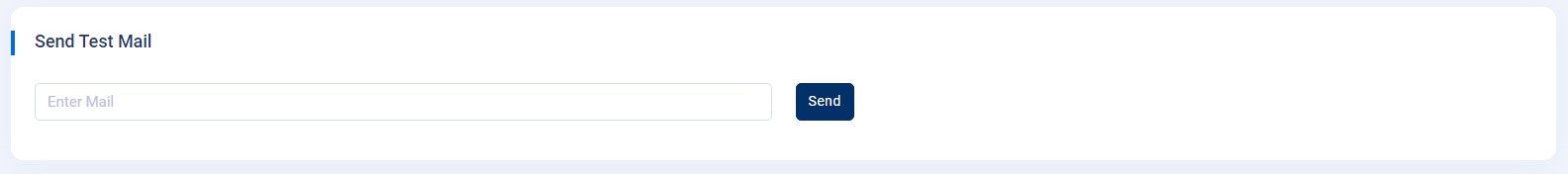
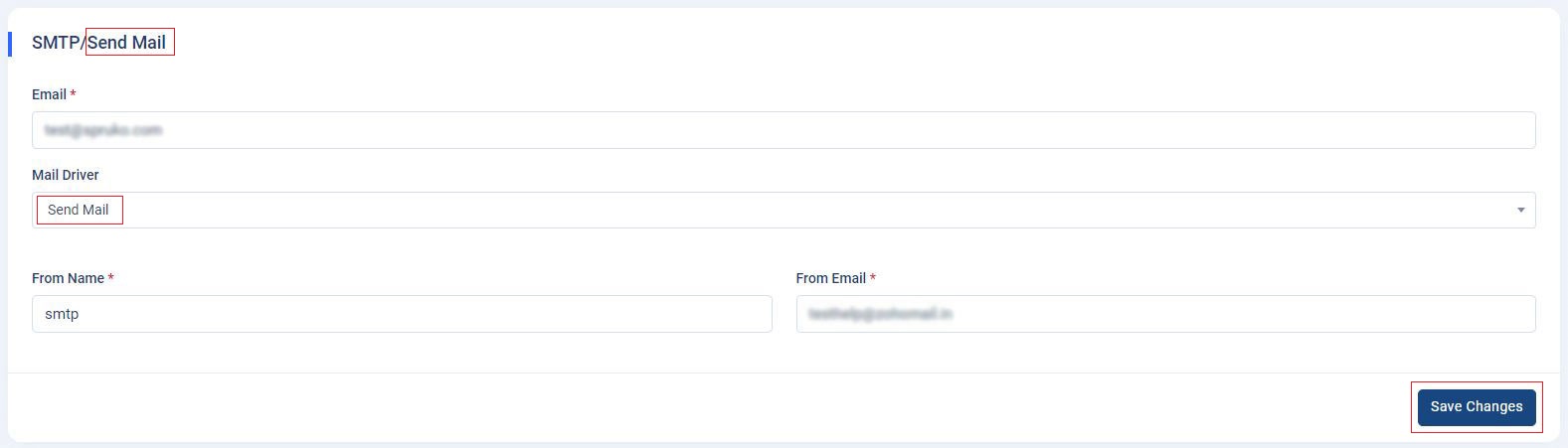
- SMTP/Send Mail/Gmail API/Microsoft : SMTP/Send Mail/Gmail API/Microsoft offers four choices: "Sendmail" ,"SMTP", "Gmail API", "Microsoft". You have the flexibility to opt for either option, but it is essential to configure the details based on your host server or the specific single-domain emails you are utilizing.
-
Sendmail : If you opt for the
"Sendmail" feature, ensure that the provided details align with
those of the host server where your application is hosted. Input
the relevant information for "Sendmail" as provided by your
hosting provider. Once entered, click on the “Save Changes”
button to implement the updates and activate this functionality.
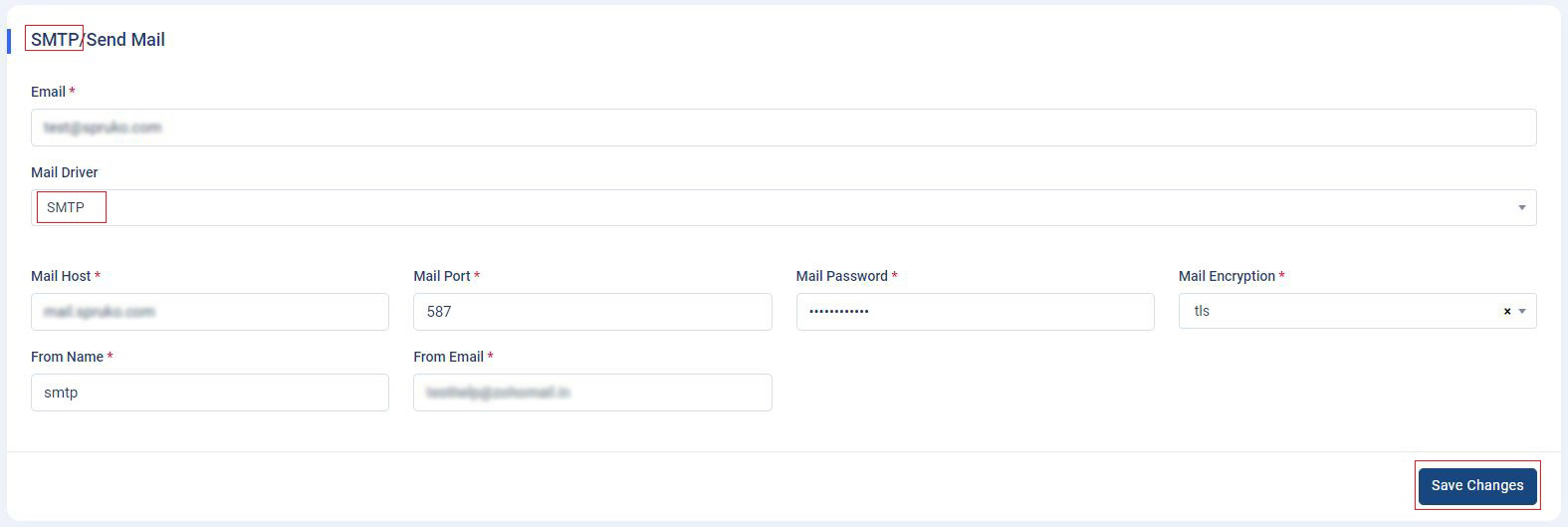
Note: Please be aware that when utilizing the "Sendmail" option, there is no requirement to input values in the "Mail Username" and "Mail Password" fields. - SMTP : If you are using the "SMTP" option, then you need to fill out all the input fields in the "SMTP" form to connect with the host that you wish to use in the application.
- To set up server SMTP settings. Please follow this guide, or for reference video click here.
-
Gmail API : If you are using
Gmail API, please follow below steps.
- Log in to the Google Cloud Console. If you already have an existing project, select it; otherwise, click Create Project to set up a new one.
- In the left-hand navigation menu, go to APIs & Services and click Enable APIs and Services. In the API Library, search for Gmail API and click Enable.
-
Once enabled, navigate to
APIs & Services → OAuth consent screen.- Select External as the user type (recommended for most cases) and click Create.
- Fill in the required fields such as App Name, User Support Email, and Developer Contact Information.
- Save and continue until the setup is complete.
-
After setting up the consent screen, go to
APIs & Services → Credentials. Click Create Credentials and select OAuth Client ID. - Choose Web Application as the application type. Provide a name (optional) and add your application's Authorized Redirect URI — use the Redirect URI provided in your application configuration. Then click Create.
- Once created, your Client ID and Client Secret will appear. Click Download JSON to save the credentials file securely.
- In your application, upload the downloaded JSON file in the designated field (usually labeled “Upload JSON File”) and click Save Changes.
- After saving, a Connect with Google or Google Consent button will appear. Click this button to authenticate and connect your application to the Gmail API.
- Once connected successfully, your application can send and receive emails using the configured Gmail API credentials.
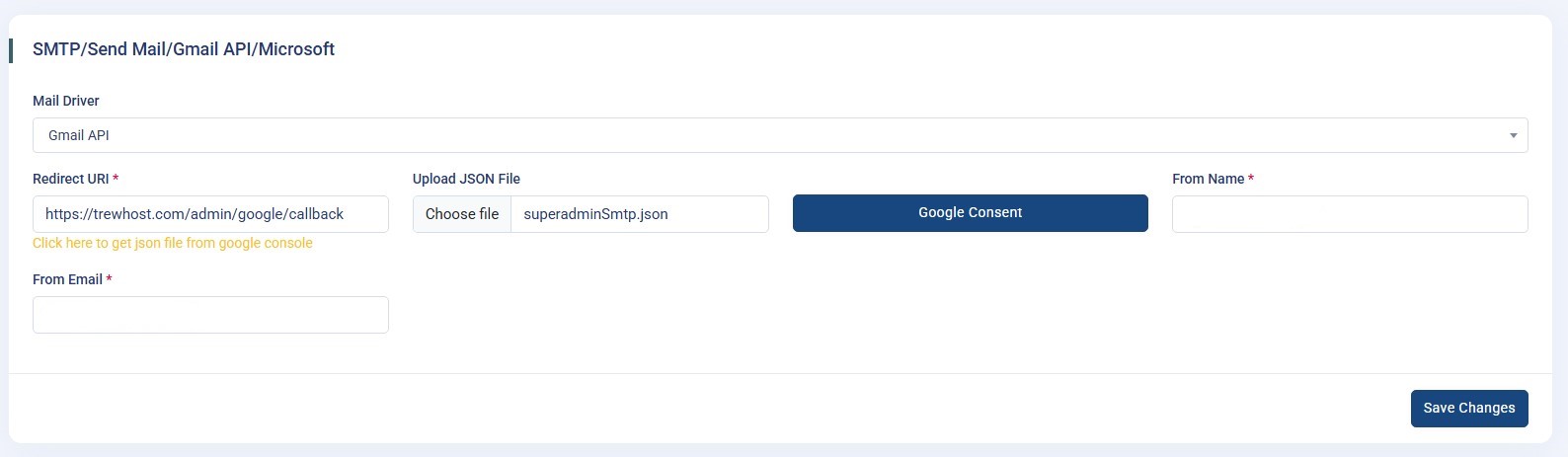
-
Microsoft : If you are using
microsoft, please follow below steps.
- Log in to the Microsoft Azure Portal using your Microsoft account.
- In the left-hand sidebar, go to Azure Active Directory. Under App registrations, click + New registration to create a new application.
-
Enter an application name (for example, “Uhelp-Smtp”)
and select the supported account type:
- Accounts in any organizational directory (Multitenant).
-
Under Redirect URI, choose
Web and enter the redirect URL provided
by your application
(for example,
https://yourapp.com/auth/microsoft/callback), then click Register. - After registration, the app’s Overview page will show your Application (Client) ID and Directory (Tenant) ID. Copy and store these values securely — you’ll need them for integration.
-
Next, create a client secret:
- Go to Certificates & Secrets in the left-hand menu.
- Under the Client Secrets tab, click + New Client Secret.
- Add a description (for example, “Production Secret”) and select an expiration period, then click Add.
- Copy the generated secret value immediately — it will be hidden after you leave the page.
-
Configure the required Microsoft Graph API permissions:
- Navigate to API Permissions → + Add a permission.
- Select Microsoft Graph → Delegated permissions.
- Add the following permissions:
openidprofileemailoffline_accessMail.Send
- Click Grant admin consent for your organization (if required).
-
In your application’s Microsoft integration settings,
enter or upload the following details:
- Client ID (Application ID)
- Client Secret
- Tenant ID
- Redirect URI (must match the one registered in Azure)
- Click the Connect with Microsoft or Microsoft Consent button in your application. A consent screen will appear — log in with your Microsoft account and approve permissions to authorize the connection.
- After successful authorization, your application will be connected to the Microsoft API, allowing it to send emails securely through Outlook using the Microsoft Graph API.
-
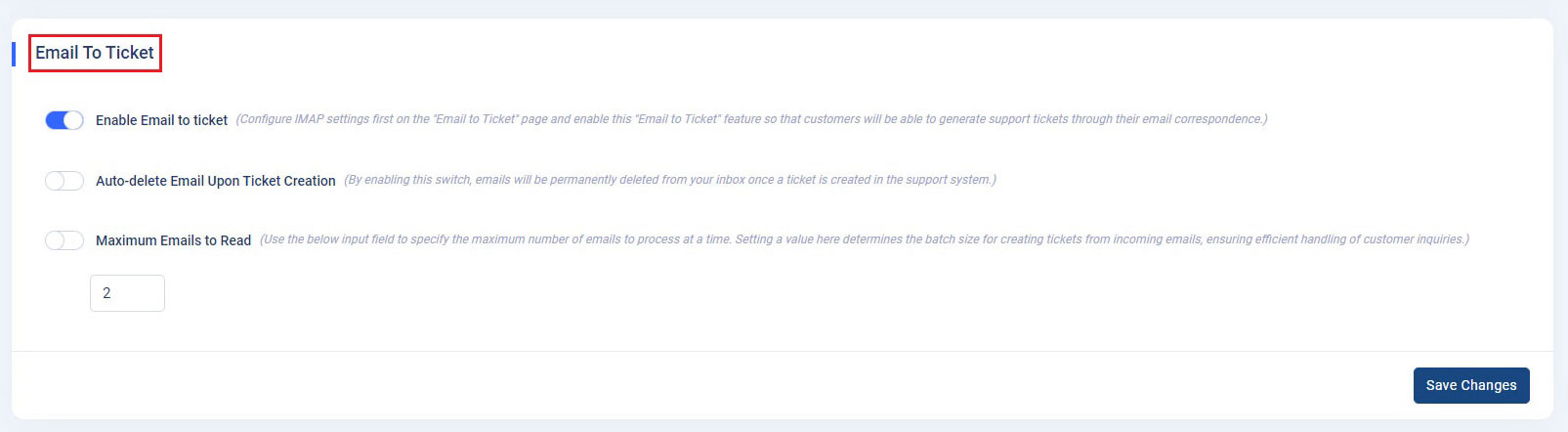
Email to Ticket Settings
To access the Email Settings, navigate to the Admin Panel > App Settings. Click on 'Email Settings' to proceed. Within the 'Email To Ticket' section, three settings are available:
- 'Enable Email to Ticket': This setting allows configuration of IMAP settings to enable customers to create support tickets via email.
- 'Auto-delete Email Upon Ticket Creation': When enabled, this setting automatically removes emails from the inbox after a ticket is generated in the support system.
- 'Maximum Emails to Read': Configure the maximum number of emails to process at once, enhancing efficiency in ticket creation from incoming inquiries."
-
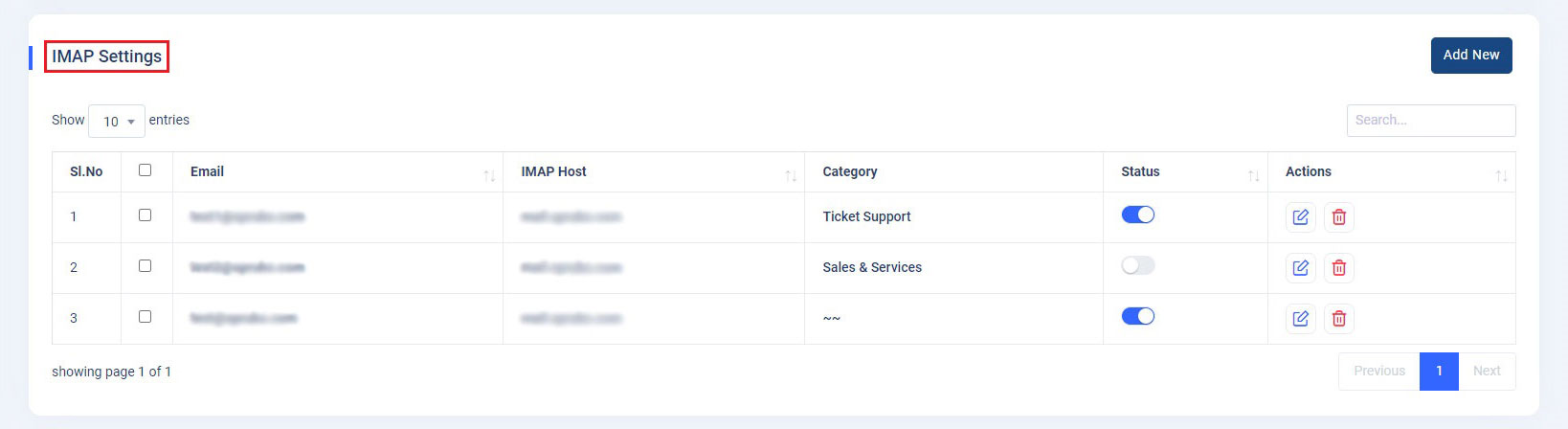
Email to Tickets
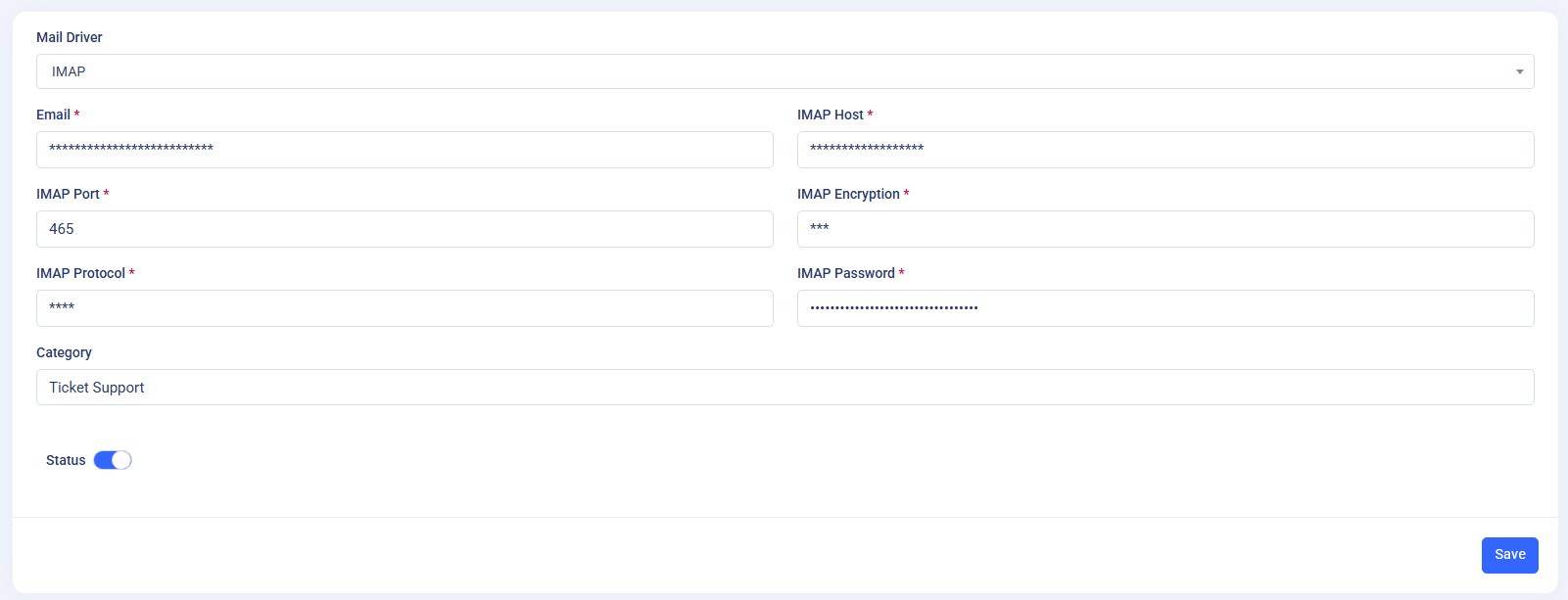
To activate this feature, go to the Admin panel and navigate to App Settings. You will be redirected to the "Email Settings" page. Scroll down to the "IMAP Settings" section, where you'll find an "Add New" button.You can select Mail Driver from the given options called Gmail, Microsoft and Imap.
-
If you select IMAP- Fill in the required details accurately and save them. If the connection is successfully established, you have configured the IMAP Settings successfully.
-
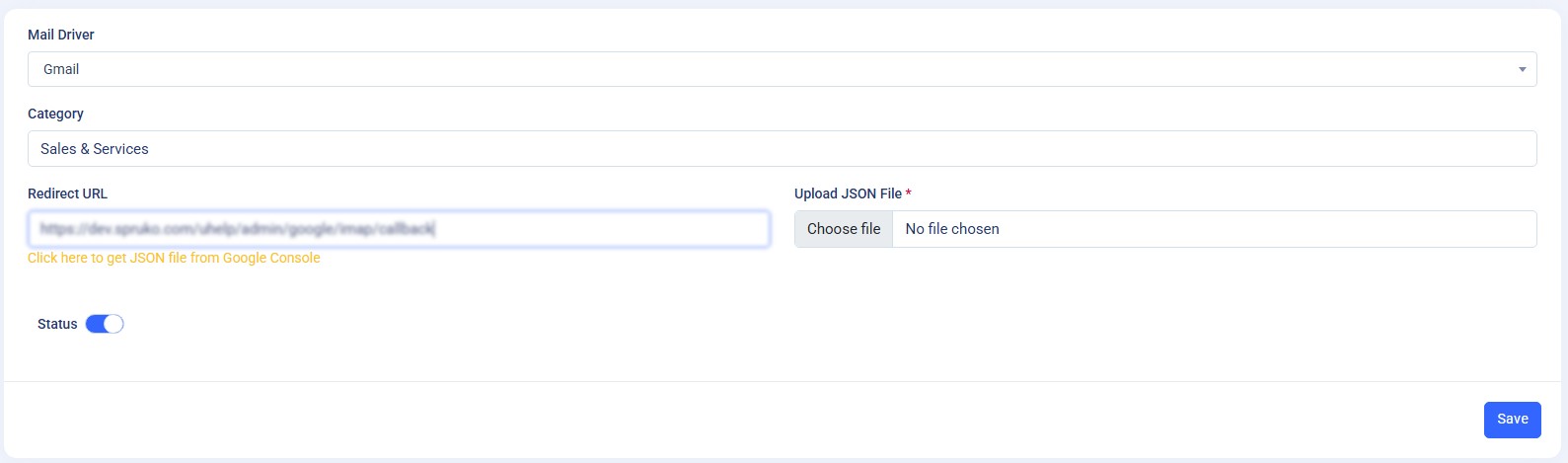
If you choose Gmail as your mail driver, you must configure the Google API by obtaining a credentials JSON file from the Google Cloud Console and uploading it to your application. Follow the steps below to complete the setup:
- Log in to the Google Cloud Console using your Google account.
- If you already have a project, select it from the top navigation bar. Otherwise, click Create Project to create a new one and give it a name (e.g., “MyApp Email Integration”).
- In the left-hand navigation menu, go to APIs & Services and click Enable APIs and Services.In the API Library, search for Gmail API and click Enable.
-
After enabling the Gmail API, navigate
to
APIs & Services → OAuth consent screen.- Select External as the user type (recommended for most use cases) and click Create.
- Enter required details like App name, User support email, and Developer contact information.
- Click Save and Continue until setup is complete.
-
Next, go to
APIs & Services → Credentials, then click Create Credentials and select OAuth Client ID. -
Choose Web Application
as the application type.
- Enter a name (for example, “Uhelp-Imap”).
- Under Authorized
Redirect URIs,
enter the redirect URL provided
in your application (for
example,
https://yourapp.com/auth/google/callback). - Click Create to generate the credentials.
- After creation, a pop-up will display your Client ID and Client Secret. Click Download JSON to save the credentials file securely on your computer.
- Return to your application’s Email Settings page. In the IMAP Configuration section, click Upload JSON File and select the downloaded credentials file obtained from the Google Cloud Console.
- Click Save Changes to apply the configuration. Once saved, a Connect with Google button will appear. Click this button to authorize and establish the connection with your Gmail account.
- Sign in with your Google account and grant permission when prompted. Once authorized, your application will be successfully connected to the Gmail API and ready to send and receive emails.
-
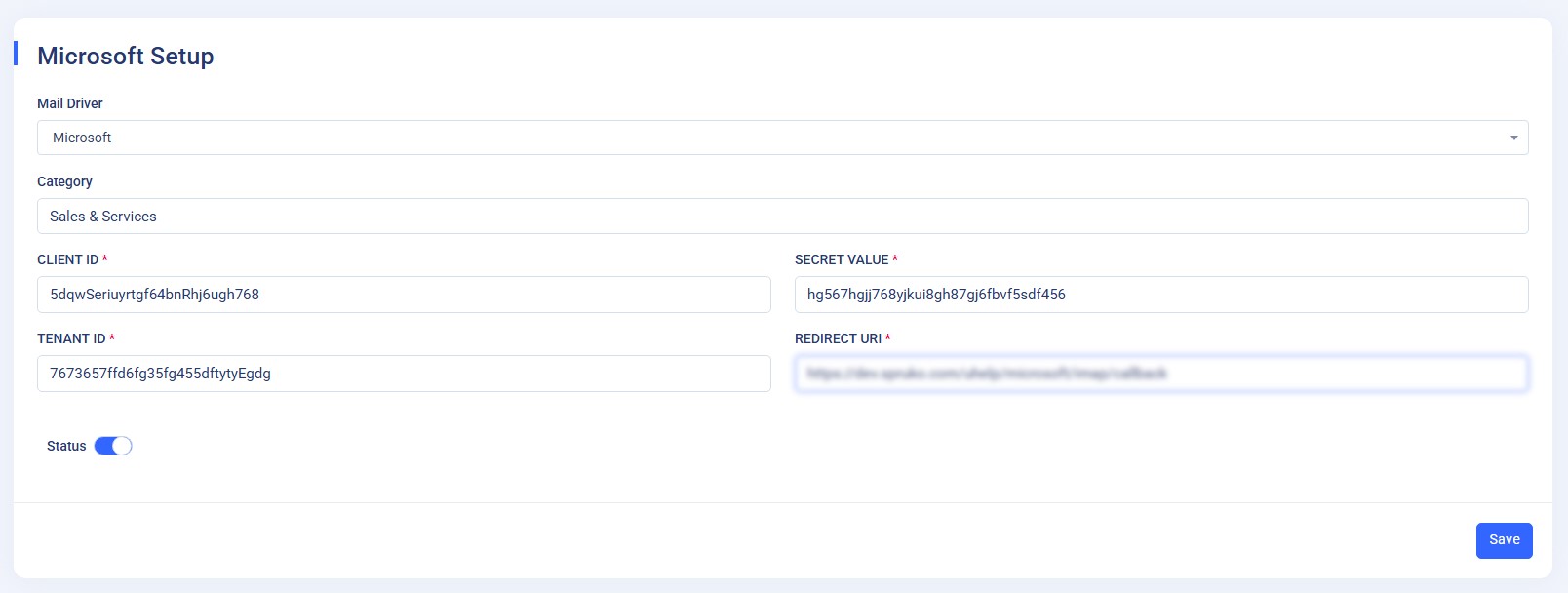
If you choose Microsoft as your mail driver, you must configure an application in the Microsoft Azure Portal and connect it to your application using the generated credentials. Follow the steps below to complete the setup:
- Log in to the Microsoft Azure Portal using your Microsoft account.
- In the left-hand navigation menu, select Microsoft Entra ID (formerly Azure Active Directory), then click App registrations.
-
Click New Registration
to create a new app.
- Enter a name for your application (e.g., UHelpSaas-Imap).
- Under Supported Account Types, choose Accounts in any organizational directory and personal Microsoft accounts (recommended for most use cases).
- In the Redirect
URI field, select
Web and enter
the redirect URL provided in
your application (for example,
https://yourapp.com/auth/microsoft/callback). - Click Register.
- Once the app is registered, go to the app overview page to view your Application (client) ID and Directory (tenant) ID. You will need these values later.
-
In the left menu, select
Certificates &
Secrets, then click
New Client Secret.
- Enter a description (e.g., Email Integration Key) and choose an expiration period.
- Click Add. Copy the generated Client Secret Value immediately — it will only be shown once.
-
Next, configure the required API
permissions:
- Go to API Permissions > Add a permission.
- Select Microsoft Graph > Delegated permissions.
- Search for and enable the
following permissions:
openidprofileemailoffline_accessMail.SendMail.ReadWrite
- Click Add Permissions, then select Grant admin consent to approve them for your tenant.
-
Once all configurations are complete,
download the app credentials:
- In the app overview page, click Manifest or Download JSON Configuration if available (or note down the Client ID, Tenant ID, and Client Secret manually).
- Return to your application’s Email Settings page. In the Microsoft Configuration section, enter Client ID, Secret Value, Tenant ID
- Click Reconnect button to authorize and link your Microsoft account and .
- After successful authorization, your application will be connected to Microsoft Graph API and can send emails securely using your Microsoft account.
The exciting part is that you can create multiple different IMAP configurations, each assigned to a specific category. For example, if you have a "Pre-Sales" category, you can link that category to a particular IMAP. Whenever customers send emails to the configured IMAP, it will automatically generate a ticket in the "Pre-Sale" category.
Email-To-Ticket feature is tried and tested with the following email service providers,
- Gmail
- Microsoft
- Yahoo
- Outlook
- Zoho
- Webmail
- Hotmail
- Aol Mail
-
-
Cron Jobs : You must run
the cron command on the cPanel server to make all
automatic functions, such as "Auto-Close Ticket," "Auto
Notification Delete," "Auto Overdue," "Auto Response,"
and "Email to Ticket."
Example :To run the cron command on your server, login to your cPanel server, scroll down and navigate to Advanced->Cron Job, and go to "Add New Cron Job" and select the "Once Per Minute (*****)" option from the "Common Settings" dropdown, and type the below command in the "Command" input field, and click on the "Add New Cron Job" button. If the process is done in the correct way, then you’ll get a message that says "cPanel successfully added the cron job".Example Command: cd /path-to-your-project && php artisan schedule:run >> /dev/null 2>&1NoteAutomatic functions of the application will not work unless you run the above cron command on your server.Please follow this guide, or for reference video click here
Let’s first understand what is IMAP?
IMAP (Internet Message Access Protocol) allows you to use a range of devices to access email stored on a server. Your hosting server must have an email plan that supports IMAP in order to use IMAP email.
9. External Chat
-
External Chat : To use a
third-party chat system, please navigate to
Admin Panel->App Setting->External Chatpage.Now integrate the third-party external chat system code into the "External Chat" text area below. And click on the above switch buttons accordingly to enable or disable the third-party external chat system on the application.
10. Security Setting
-
Security Setting : In this
application, we implemented three different types of security
settings: "Country Block/Unblock", "Admin Country
Block/Unblock", and "DOS Attack". And they are unique in their
functionality. To use this setting, navigate to the
Admin Panel->App Setting->Security Settingpage and follow the below process. -
Country Block/Unblock : This
setting is used to "Block" or "Allow" countries from accessing
the application of the main site URL: https://app.spruko.com/mydesk,
which is on the visitor's side.
If you want to "Block" or "Allow" a country or multiple countries, then click and select the countries from the "Select Country" dropdown and click on the "Save changes" button to block or allow the countries you selected.
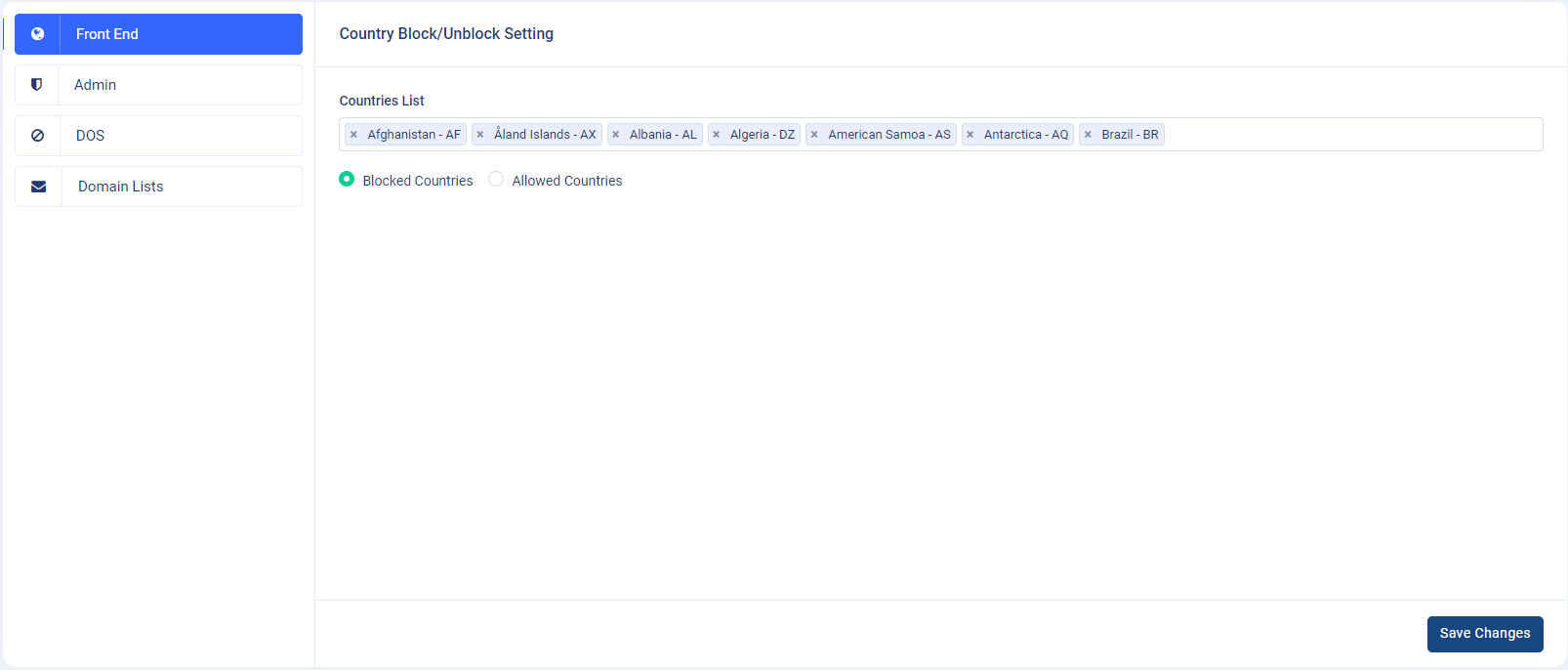
By default, all countries are allowed to use the application. If the "Select Country" dropdown is left empty, then any country can access the application's main site URL: https://app.spruko.com/mydesk.
-
Admin Country Block/Unblock :
This setting is used to "Block" or "Allow" countries
from accessing the application of the admin URL: https://app.spruko.com/mydesk/admin,
which is on the admin side.
If you want to "Block" or "Allow" a country or multiple countries, then click and select the countries from the "Select Country" dropdown and click on the "Save changes" button to block or allow the countries you selected.
By default, all countries are allowed to use the application. If the "Select Country" dropdown is left empty, then any country can access the application's admin URL:https://app.spruko.com/mydesk/admin.
Note: You are not allowed to block your own country. - DOS Attack Setting : This setting secures the application from denial-of-service (DoS) attacks.
-
You have two input fields in the DoS attack setting. The first input indicates "Attempts" and the second input indicates "Seconds." For example, if 10 "attempts" in 30 "seconds" come from a particular IP address, then that IP address will be blocked or the user may be redirected to a captcha page, depending on the option you choose.
Example: First enable the toggle switch button, choose the "View Captcha" option from the "DOS Attack Setting" section and set 10 in the first input field ("Attempts") and 30 in the second input field ("Seconds") and click on the "Save Changes" button. If a user tries to access the application 10 times in 30 seconds, his or her IP address will be temporarily blocked and he or she will be redirected to the captcha page. Or if you choose "Block IP Address", then it will block the IP address permanently. If you don't want to use this feature, simply click on the above toggle switch button to disable it.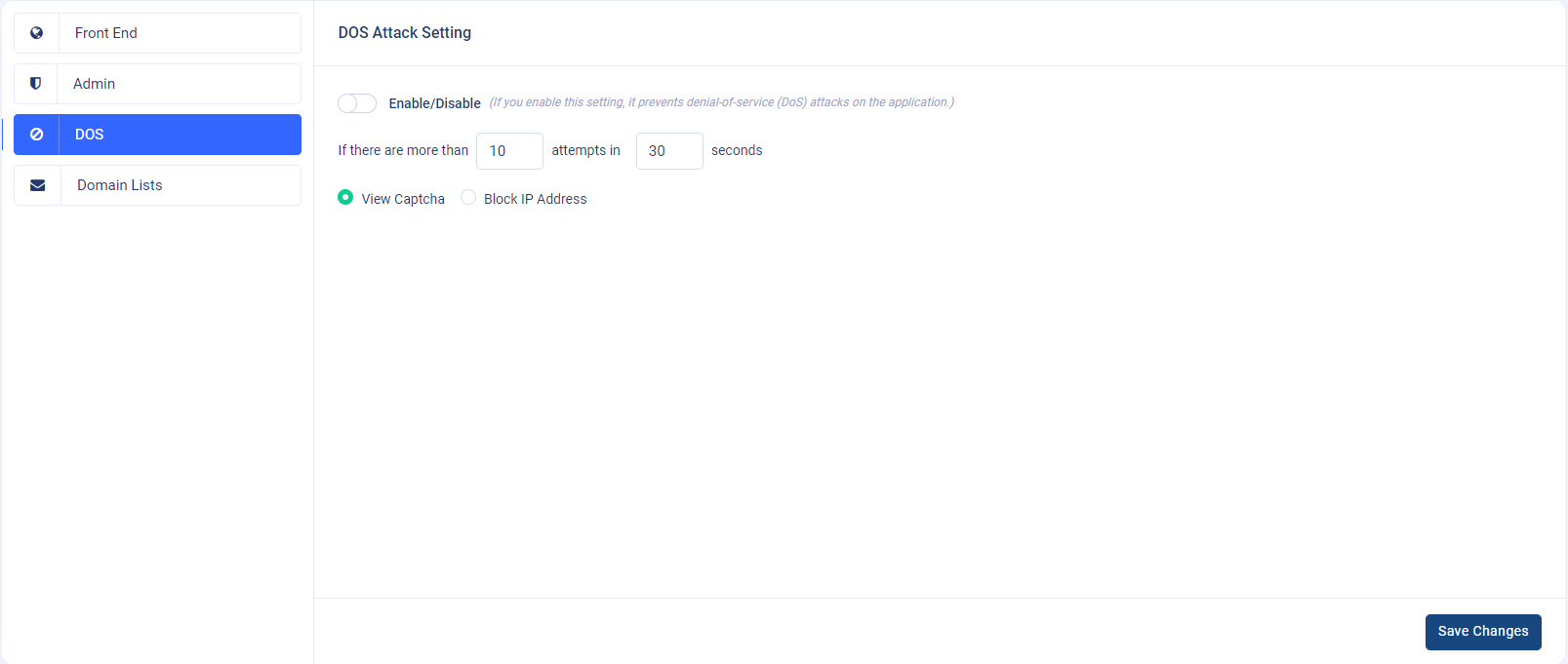
- Domain list : This setting allows you to block specific domain email's for guest users only while creating ticket.
-
You have to give the list of allowed domain's or list of blocked domain's by coma(,) saperated values. This will block or only allow the specified domain's
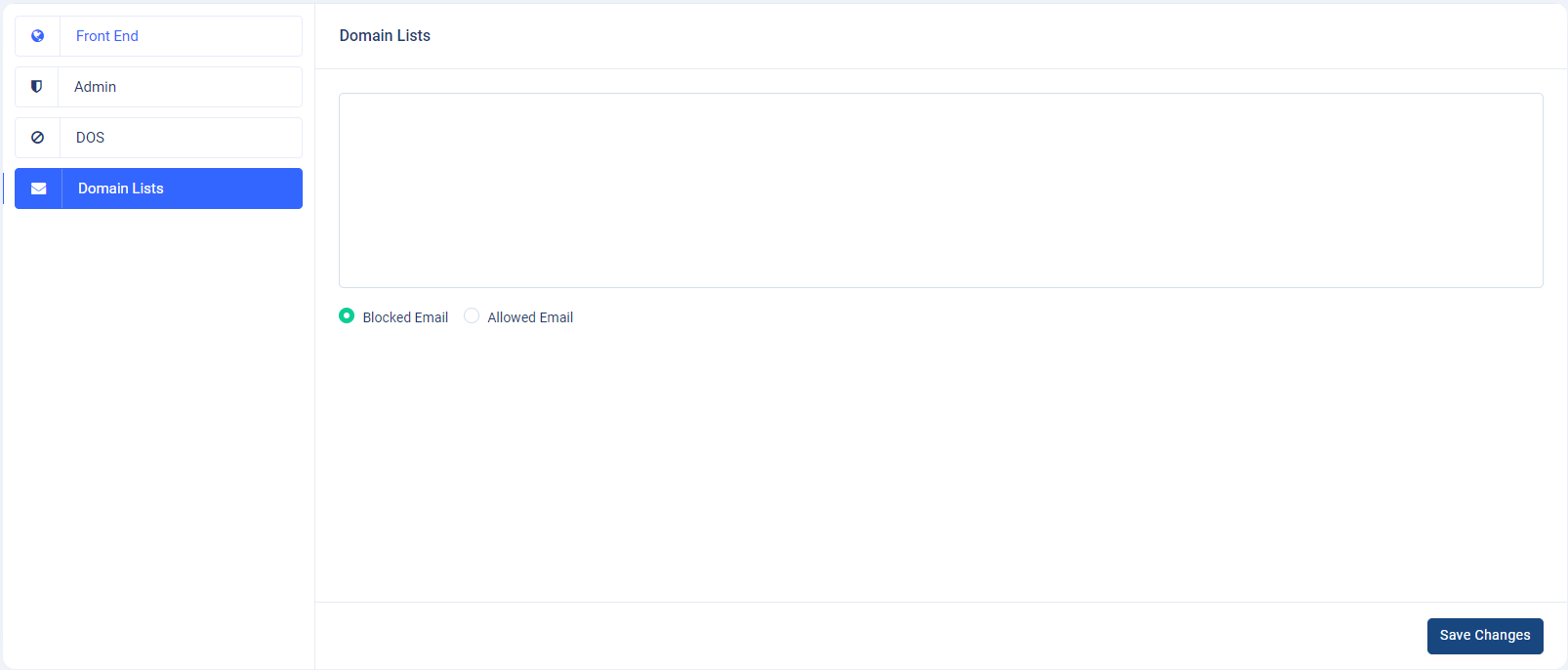
How do I set up DoS attack settings and get a basic overview?
How do I set up Domain List and block some particular domain's
11. IP List
-
IP List : All temporary and
permanently blocked IP addresses are displayed in the "IP List"
table, and you can also add IP addresses manually by clicking on
the "Add IP Address" button in the "IP List" table.
When you click on the "Add IP Address" button in the "IP List" table, a modal pop-up will appear with the "IP" input field and "Type". Fill in the input field and select the option from the "Type" and click on the "Save" button to apply the changes.
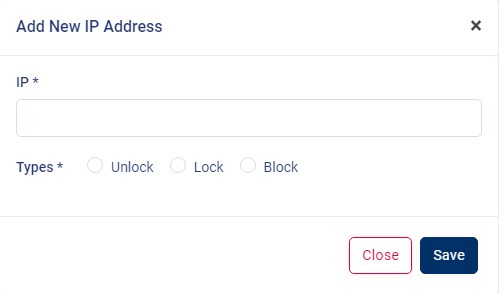
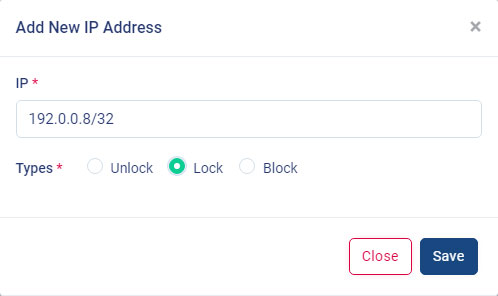
- Unlock : You can "unlock" and make the IP addresses normal so users can access the application.
- Lock : You can "Lock" the IP addresses and make users to access the application temporally with captcha.
-
Block : You can "Block" IP
addresses, and users won't be able to access the application
permanently until the IP addresses are "unlocked."
Here there are three more options. Edit, Delete, and Reset in the “Actions” column on the "IP List" table.
- Edit : By clicking on the edit option in the “Actions” column you update the IP addresses using the above options.
- Delete : You can also delete the records of IP addresses permanently. So that users are allowed to access the application.
-
Reset : You can also reset the IP
addresses. It works the same as the unlock option so that users
are allowed to access the application.
Note: Please click on the “Save” button after you add or edit the IP addresses.
12. Bot Response Setting
-
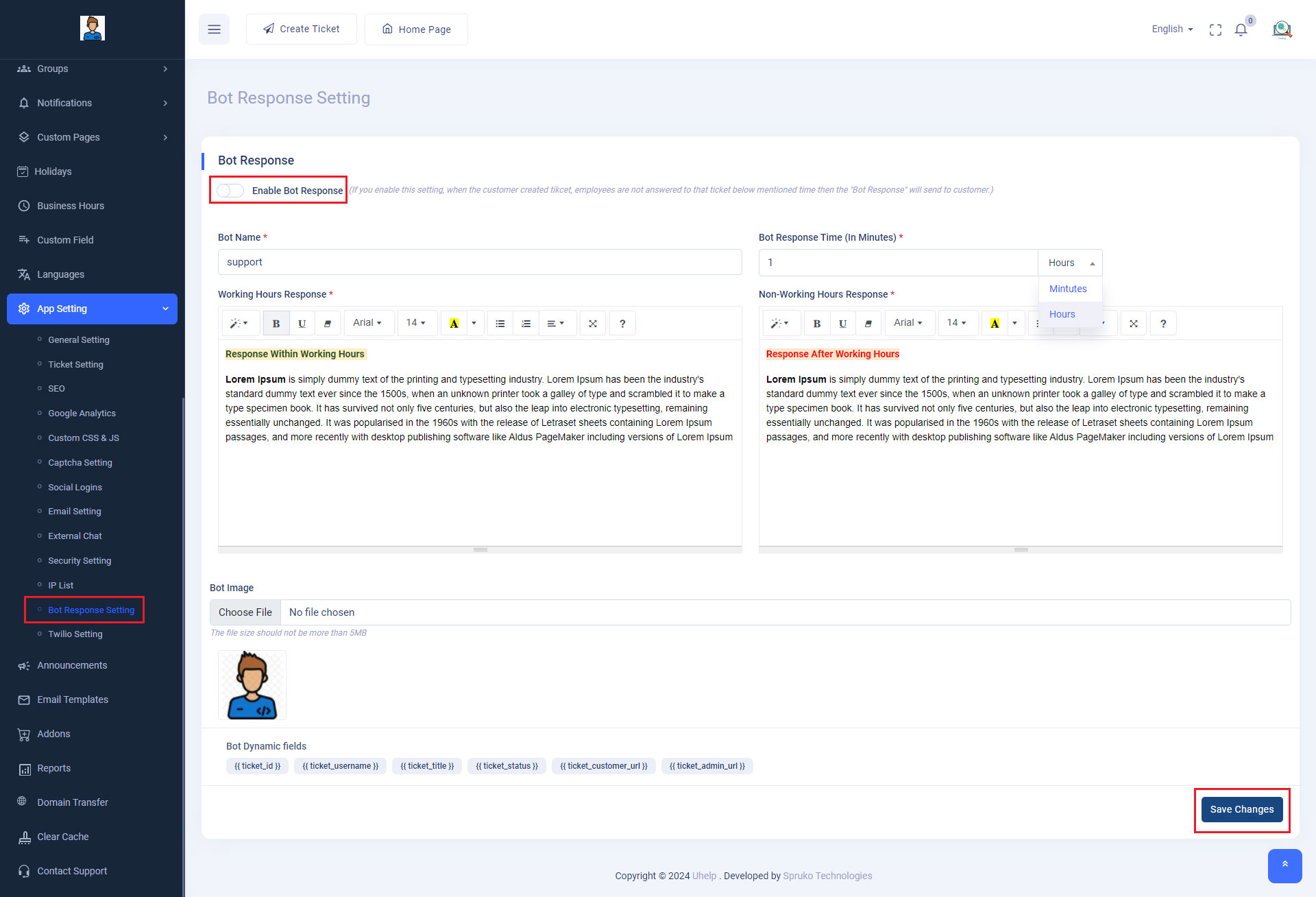
Introduction: The "Bot Response
Setting" feature has been implemented, empowering superadmins to
establish response times for automated bot responses. The bot
generates predefined responses if agents fail to respond within
a specified time during working hours, with separate
configurations for non-working hours.
-
Configuration Steps:.
Functionality Overview:.
- To utilize this feature, navigate to the
Admin Panel -> App Settings -> Bot Response Settingpage. - Toggle the "Enable Bot Response" switch and click on the "Save Changes" button at the bottom right corner to activate the feature. If enabled, when a customer creates a ticket and employees fail to respond within the specified time, the bot generates a response.
- Fill in the following details:
- "Bot Name": Provide a name for the bot.
- "Bot Response Time (In Minutes/Hours)": Set the time frame within which the bot response will be triggered.
- "Working Hours Response" and "Non-Working Hours Response": Customize the response messages for working and non-working hours, respectively.
- "Bot Image": Optionally, upload an image for the bot.
- Utilize dynamic variables like "{{ ticket_id }}" to display actual content dynamically.
- During business hours, if a ticket is created and remains unanswered by agents, the bot will respond with the message specified in the "Working Hours Response" within the defined response time.
- During non-working hours or during holidays, the bot will send the message specified in the "Non-Working Hours Response" within the specified response time.
- Ensure that configurations align with business hours and holiday settings for optimal automated response management.
- To utilize this feature, navigate to the
13. Twilio Setting
-
Twilio Settings Introduction :
We've introduced the "Twilio Settings" page in the
application to enable receiving ticket updates via SMS. Upon
admin configuration and activation of the Twilio account,
customers are prompted to verify their mobile numbers to begin
receiving ticket updates.

-
Configuration Steps :.
- Navigate to the
Admin Panel -> App Settings -> Twilio Settingspage. - In the "Twilio Settings" section, fill in the three input fields ("Twilio Authentication Id," "Twilio Authentication Token," and "Twilio Phone Number") with the appropriate details following the official Twilio documentation.
- Enable the toggle switch at the top right corner and save the settings to activate Twilio on the application.
- Customers will then be asked to verify their mobile numbers to receive ticket updates via SMS.
- Navigate to the
-
Message Template Introduction :
Within the "Message Template" section, users can
customize message templates for various ticket-related
notifications.

-
Template Customization:.
- Message to customer when a ticket is created
- Message to customer when they receive a reply to the ticket
- Message to customer when the ticket is closed
- Message to customer when the ticket is auto-closed
- Message to customer when there is no response to the ticket
Users can tailor these templates according to their preferences. The customized templates will be sent as ticket updates to customers.
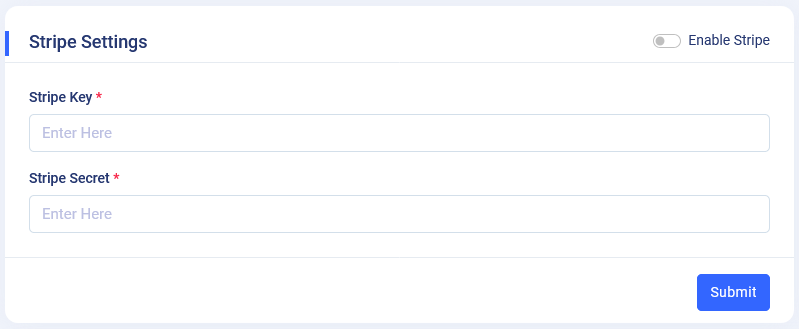
14. Payment Gateways
- Payment Gateways Introduction : We have introduced the "Payment Gateways" page to facilitate payments within the application, allowing users to make payments for custom invoices.
-
Configuration Steps :.
- Navigate to the
Admin Panel -> App Settings -> Payment Gatewayspage. - In this page you can see 2 sections one is for stripe payment setup and other is for paypal payment setup. After submitting the key and secret in the respective fields you can able to integrate payment gateways in the application.
- Navigate to the
- Navigate to the Dashboard.
- Under REST API apps, click Create App.
- Provide a name for the app and choose a sandbox account (if testing) or production account (if live).
- Once the app is created, you'll be taken to the app's details page.
- Here, you'll see the Client ID and Secret under the Sandbox (or Live) tab, depending on your app’s environment.
- Copy the Client ID and Secret for use in your application to authenticate PayPal transactions.
- Navigate to the API Keys.
- In the left-hand menu, click on Developers.
- Under the Developers section, select API keys.
- On the API keys page, you'll see both your Publishable key and Secret key listed under Standard keys.
- By default, the Secret key is hidden. Click on Reveal live key to view it.
- To toggle between test and live API keys, use the Viewing test data switch in the left-hand menu.
- Ensure you're using the appropriate keys for your environment: test keys for development and live keys for production. Keep your Secret key confidential and do not expose it in client-side code. It's recommended to use secure key management practices to protect your API keys. For more details, refer to Stripe's API key documentation.
-
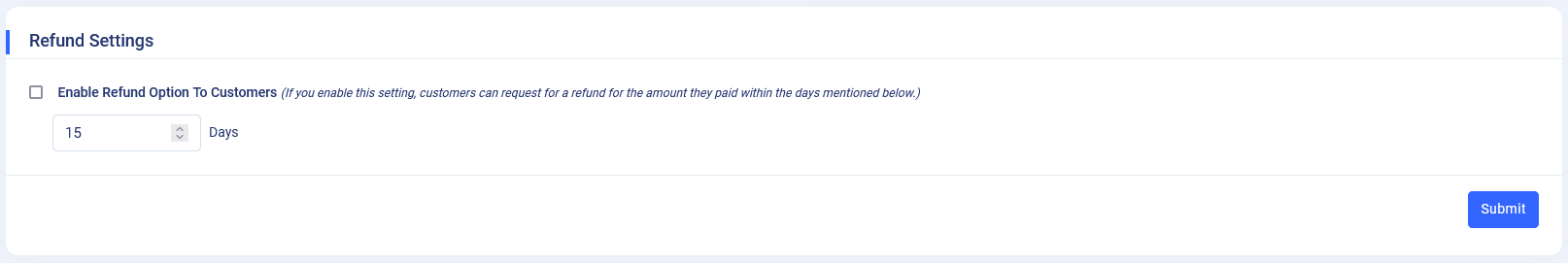
Refund Option :.
- This setting allows you to enable or disable the refund option for customers. If enabled, you can specify the number of days within which the refund option will be available.
-
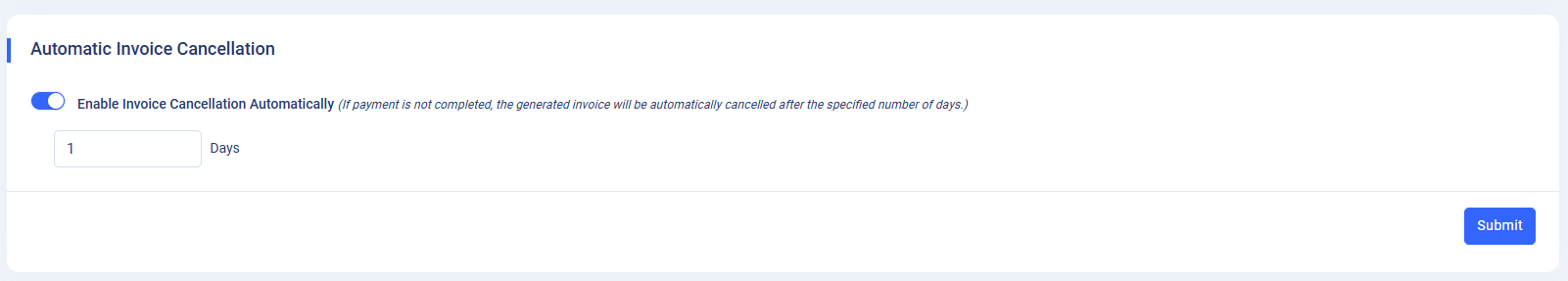
Automatic Invoice Cancellation :.
- This setting allows you to enable or disable the Auto invoice cancel option for generated invoices if payment is not processed by customer . If enabled, you can specify the number of days within which the invoice should get cancelled.
-
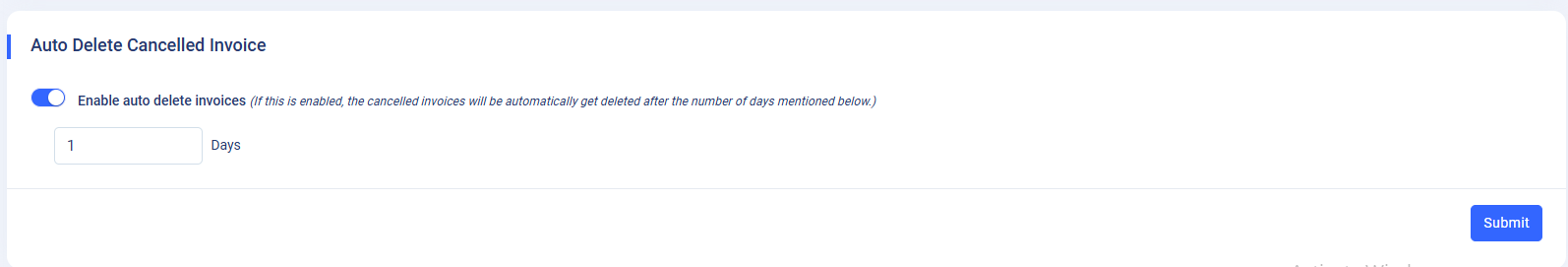
Auto Delete Cancelled Invoice :.
- This setting allows you to enable or disable the delete option for cancelled invoices to manage database. If enabled, you can specify the number of days within which the invoice should get deleted.
To generate a PayPal client ID (key) and secret, follow these steps:
Go to the PayPal Developer Portal and log in with your PayPal account credentials.
To generate Stripe API keys (publishable and secret) for your application, follow these steps:
Visit the Stripe Dashboard and sign in with your credentials.
15. AI Setup
-
AI Setup Introduction :
We have introduced the "AI Setup" page to enable AI in this application. For this, you need to generate a Gemini API key in Google AI Studio https://ai.google.dev/gemini-api/docs/api-key. Here, you can generate an API key by clicking on "Get a Gemini API key in Google AI Studio". This will ask you to log in using a Google account.
After logging in, you'll be redirected to https://aistudio.google.com/app/apikey. There, you will find a button "Create API Key". On clicking this, a modal will appear where you can select an existing project, or you can click on "Create API Key in new project".
This will generate a new API key, which you can then use in the application.
Please enter the latest gemini model.
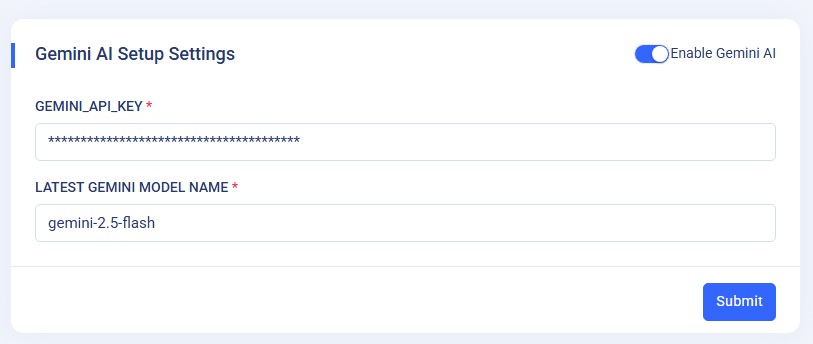
By enabling this setting, you can utilize the Gemini API key on the ticket view page. This allows users to either generate new text or improve existing text directly within the ticket interface. The Gemini API provides powerful language processing capabilities to assist in creating or enhancing content automatically based on the ticket context.
16. SSO Setup
-
SSO Setup Introduction :
Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials. This simplifies authentication, enhances security, and improves user experience.
Seamless sign-in to uhelp (secondary) if a user is already logged into the Main app.
Works across any domains/subdomains (no third-party cookies or iframes needed).
Minimal dependencies, easy to port to other stacks.
The SSO Contract (what uhelp expects)- Endpoint: expose GET /sso/redirect.
- Inputs (query):
- client_id — e.g. UHELP
- return_to — absolute URL to uhelp
- state — opaque nonce from uhelp
- Auth: require the user is logged in on Main (first-party session).
- Allow-list: verify return_to origin is in an allow-list (exact scheme://host[:port]).
- Token: mint a short-lived HS256 token with these claims:
- sub (user id), email, name, firstname, lastname
- iat, exp (TTL ≈ 60s)
- jti (unique id)
- client_id (must match uhelp’s)
Example code for Laravelclass SsoController extends Controller { // Hardcoded config for demo/docs (move to env/DB in prod) private const CLIENT_ID = 'UHELP'; private const SECRET = 'paste-a-long-random-secret-here'; private const ASSERTION_TTL = 60; // seconds // Exact origins only (scheme://host[:port]) — no paths, no trailing slash private const ALLOWED_RETURN_TO = [ 'http://localhost', // 'https://uhelp.example.com', ]; /** * GET /sso/redirect?client_id=UHELP&return_to=<ABS uhelp>/admin/t/{tenant}/sso/consume&state=<nonce> */ public function redirect(Request $r) { $clientId = (string) ($r->query('client_id', self::CLIENT_ID)); $returnTo = (string) $r->query('return_to', ''); $state = (string) $r->query('state', ''); if (! $this->allowedReturnTo($returnTo)) { abort(400, 'return_to not allowed'); } // Require user to be logged into Main (first-party session) if (! Auth::check()) { return redirect()->guest(route('login', ['intended' => url()->full()])); } // Build short-lived HS256 assertion $user = Auth::user(); $now = time(); $exp = $now + self::ASSERTION_TTL; $claims = [ 'sub' => (string) $user->getAuthIdentifier(), 'email' => (string) ($user->email ?? ''), 'name' => (string) ($user->name ?? ''), 'firstname' => (string) ($user->firstname ?? ''), 'lastname' => (string) ($user->lastname ?? ''), 'iat' => $now, 'exp' => $exp, 'jti' => (string) Str::uuid(), 'client_id' => $clientId, ]; $token = $this->sign($claims, self::SECRET); // Top-level GET redirect back to uhelp (keeps uhelp's session cookie) $qs = http_build_query(['assertion' => $token, 'state' => $state], '', '&', PHP_QUERY_RFC3986); $sep = str_contains($returnTo, '?') ? '&' : '?'; return redirect()->away($returnTo.$sep.$qs); } /* ------------------ helpers ------------------ */ private function sign(array $payload, string $secret): string { $b64 = static function ($data): string { if (is_array($data)) { $data = json_encode($data, JSON_UNESCAPED_SLASHES); } return rtrim(strtr(base64_encode($data), '+/', '-_'), '='); }; $h = $b64(['alg' => 'HS256', 'typ' => 'SSO']); $p = $b64($payload); $s = $b64(hash_hmac('sha256', "$h.$p", $secret, true)); return "$h.$p.$s"; } private function allowedReturnTo(?string $url): bool { if (! $url) return false; $u = parse_url($url); if (! $u || empty($u['scheme']) || empty($u['host'])) return false; // only allow http/https schemes $scheme = strtolower($u['scheme']); if (!in_array($scheme, ['http', 'https'], true)) return false; $origin = strtolower($scheme.'://'.$u['host'].(isset($u['port']) ? ':'.$u['port'] : '')); return in_array($origin, array_map('strtolower', self::ALLOWED_RETURN_TO), true); } }Example code for Node.js// server.mjs (run with: node server.mjs) import express from 'express'; import crypto from 'crypto'; import { requireLogin } from './auth.js'; const app = express(); /** ---- Hardcoded config for demo (move to env/DB for prod) ---- */ const CLIENT_ID = 'UHELP'; const SECRET = 'paste-a-long-random-secret-here'; // must match uhelp’s verifier const TTL_SECONDS = 60; const ALLOWED_RETURN_TO = new Set([ 'http://localhost', // exact origins only; no paths // 'https://uhelp.example.com', ]); /** ------------------------------------------------------------- */ const originOf = (u) => { try { const x = new URL(u); return `${x.protocol}//${x.host}`; } catch { return null; } }; const b64url = (buf) => buf.toString('base64').replace(/\+/g,'-').replace(/\//g,'_').replace(/=+$/,''); /** * GET /sso/redirect * Query: client_id, return_to (ABS URL), state (nonce from uhelp) */ app.get('/sso/redirect', requireLogin, (req, res) => { const clientId = (req.query.client_id || CLIENT_ID).toString(); const returnTo = (req.query.return_to || '').toString(); const state = (req.query.state || '').toString(); // 1) Validate return_to origin const origin = originOf(returnTo); if (!origin || !ALLOWED_RETURN_TO.has(origin)) { return res.status(400).send('return_to not allowed'); } // 2) Require user is logged in (handled by requireLogin) const user = req.user; // { id, email, name, ... } // 3) Build short-lived HS256 assertion const now = Math.floor(Date.now() / 1000); const claims = { sub: String(user.id), email: String(user.email || ''), name: String(user.name || ''), iat: now, exp: now + TTL_SECONDS, jti: crypto.randomUUID(), client_id: clientId, // optional extras to match your PHP: firstname/lastname, etc. // firstname: user.firstName || '', // lastname: user.lastName || '', }; const header = { alg: 'HS256', typ: 'SSO' }; const h = b64url(Buffer.from(JSON.stringify(header))); const p = b64url(Buffer.from(JSON.stringify(claims))); const s = b64url(crypto.createHmac('sha256', SECRET).update(`${h}.${p}`).digest()); const token = `${h}.${p}.${s}`; // 4) Top-level GET redirect back to uhelp const sep = returnTo.includes('?') ? '&' : '?'; const location = `${returnTo}${sep}assertion=${encodeURIComponent(token)}&state=${encodeURIComponent(state)}`; return res.redirect(location); }); // Health app.get('/', (_, res) => res.send('Main SSO up')); const PORT = process.env.PORT || 3000; app.listen(PORT, () => console.log(`Main listening on http://localhost:${PORT}`));Example code for Ruby# config/routes.rb Rails.application.routes.draw do get '/sso/redirect', to: 'sso#redirect' end # app/controllers/sso_controller.rb class SsoController < ApplicationController # 🔒 Hardcoded for docs/demo (move to ENV/DB in prod) CLIENT_ID = 'UHELP' SECRET = 'paste-a-long-random-secret-here' # must match uhelp TTL = 60 # seconds ALLOWED = ['http://localhost'] # exact origins only (scheme://host[:port]) # GET /sso/redirect?client_id=UHELP&return_to=<ABS uhelp>/admin/t/{tenant}/sso/consume&state=<nonce> def redirect client_id = (params[:client_id].presence || CLIENT_ID).to_s return_to = (params[:return_to].presence || '').to_s state = (params[:state].presence || '').to_s unless allowed_return_to?(return_to) render plain: 'return_to not allowed', status: :bad_request and return end # ✅ Require the user is logged in on Main # Example with Devise: unless user_signed_in? redirect_to new_user_session_path(intended: request.original_url) and return end # Build short-lived HS256 assertion now = Time.now.to_i claims = { sub: current_user.id.to_s, email: current_user.email.to_s, name: (current_user.respond_to?(:name) ? current_user.name.to_s : ''), iat: now, exp: now + TTL, jti: SecureRandom.uuid, client_id: client_id, # optional extras if you like: # firstname: current_user.first_name.to_s, # lastname: current_user.last_name.to_s, } token = sign_hs256(claims, SECRET) # Top-level GET back to uhelp qs = Rack::Utils.build_query(assertion: token, state: state) sep = return_to.include?('?') ? '&' : '?' redirect_to "#{return_to}#{sep}#{qs}" end private def allowed_return_to?(url) uri = URI.parse(url) rescue nil return false unless uri&.scheme && uri&.host origin = "#{uri.scheme}://#{uri.host}" origin << ":#{uri.port}" if uri.port && ![80,443].include?(uri.port) ALLOWED.map!(&:downcase) ALLOWED.include?(origin.downcase) end def sign_hs256(payload, secret) header = { alg: 'HS256', typ: 'SSO' } h = b64url(header.to_json) p = b64url(payload.to_json) s = b64url(OpenSSL::HMAC.digest('sha256', secret, "#{h}.#{p}")) "#{h}.#{p}.#{s}" end def b64url(bytes_or_str) s = bytes_or_str.is_a?(String) ? bytes_or_str : bytes_or_str.to_s Base64.urlsafe_encode64(s).delete('=') end endBy enabling this setting, you can utilize the Gemini API key on the ticket view page. This allows users to either generate new text or improve existing text directly within the ticket interface. The Gemini API provides powerful language processing capabilities to assist in creating or enhancing content automatically based on the ticket context.